
Microsoft’s April 2024 Patch Tuesday, 149 Vulnerabilities Patched, Inc...
Microsoft’s April 2024 Patch Tuesday, 149 Vulnerabilities Patched, including 2 Zero-Day Vulnerabilities Microsoft’s April 2024 Patch Tuesday was a substantial release addressing a total of 149 securit...

How to Monitor Your Supply Chain’s Dark Web Activities?
How to Monitor Your Supply Chain’s Dark Web Activities? As organizations rely on complex networks of suppliers and vendors to deliver goods and services, ensuring the integrity and resilience of these...

Top 10 CTI Blogs You Need to Follow
Top 10 CTI Blogs You Need to Follow CTI blogs play an important role in keeping security professionals up to date on the latest threats, trends, and defensive strategies, providing in-depth analysis, ...

Top 10 Threat Intelligence Podcasts
Top 10 Threat Intelligence Podcasts Podcasts provide an easy and effective way to stay up to date on the threat intelligence landscape. They cover a wide range of topics, including insights into the m...

Latest Dark Web Sales: Exploits, 0-Days, Financial & Government Data L...
Latest Dark Web Sales: Exploits, 0-Days, Financial & Government Data Leaks, DarkVR Service The SOCRadar Dark Web Team’s recent discoveries reveal a range of concerning cyber threats. These include...

Cybersecurity Risks During 2024 Indian General Elections
Cybersecurity Risks During 2024 Indian General Elections General elections in India will be held from April 19 to June 1, 2024. In the context of election security in cyberspace, a couple of points ca...
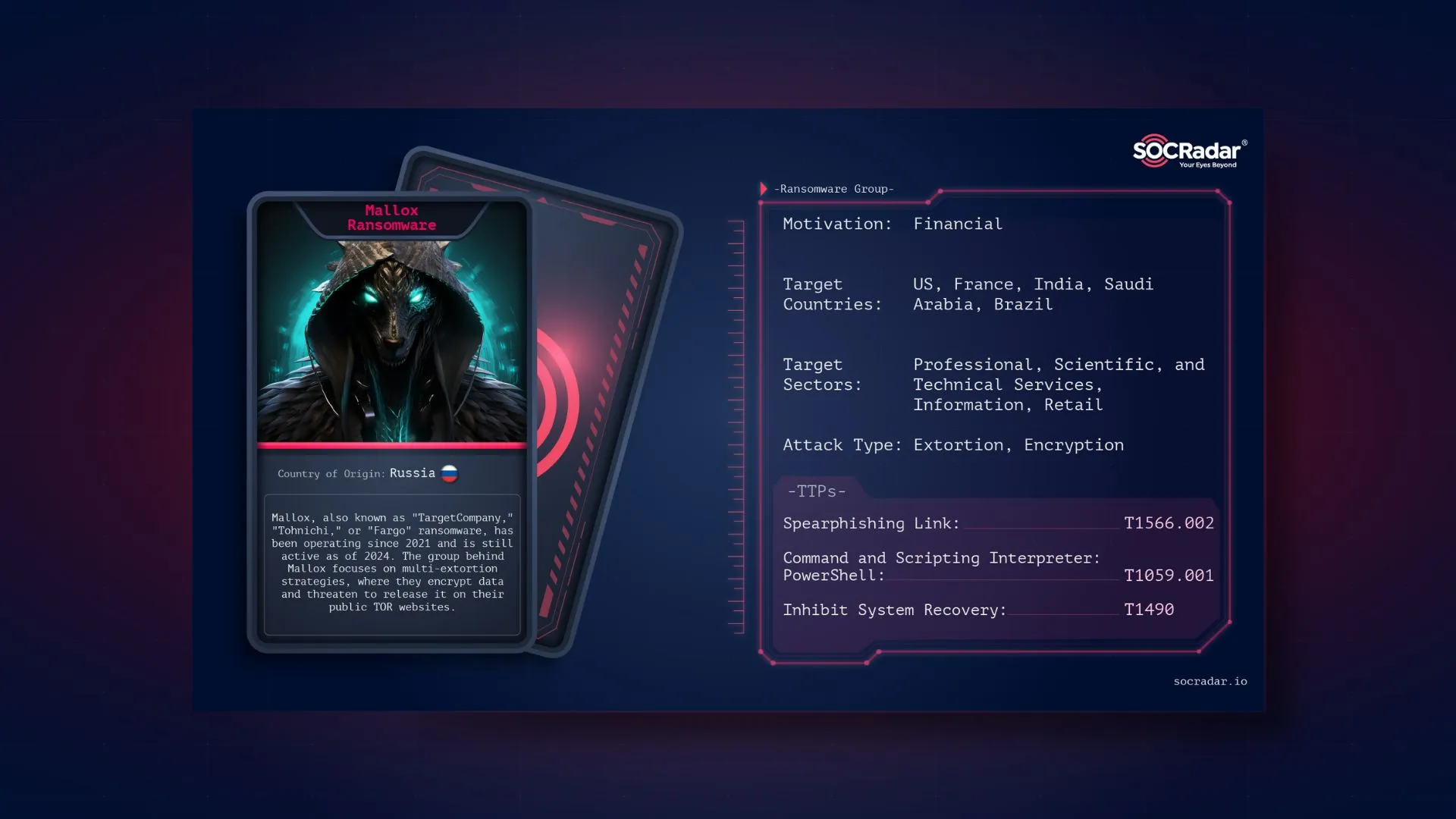
Dark Web Profile: Mallox Ransomware
Dark Web Profile: Mallox Ransomware Mallox, a strain of ransomware and a group with the same name, encrypts its victims’ data and subsequently demands a ransom, typically in cryptocurrency, in return ...

CISA Adds SOCRadar Labs to its Resources & Tools
CISA Adds SOCRadar Labs to its Resources & Tools In a significant move to bolster cybersecurity resilience, the Cybersecurity and Infrastructure Security Agency (CISA) has officially included SOC...

Dark Web Profile: DonutLeaks
Dark Web Profile: DonutLeaks In 2022, the DonutLeaks group emerged as a significant player, demonstrating a sophisticated approach to data extortion. Linked to cyber incidents targeting notable enterp...

Cybersecurity Challenges in 2024 United Kingdom’s Elections
Cybersecurity Challenges in 2024 United Kingdom’s Elections Cybersecurity challenges are expected to play a significant role in the upcoming United Kingdom elections in 2024. As the world becomes more...

Ivanti Connect Secure and Policy Secure Gateways Vulnerable to DoS and...
Ivanti Connect Secure and Policy Secure Gateways Vulnerable to DoS and Code Execution (CVE-2024-21894) Ivanti recently released patches to fix multiple vulnerabilities found in their popular Connect S...

Shedding Light on the Ancient Continent: Insights from Southern Africa
Shedding Light on the Ancient Continent: Insights from Southern Africa Today’s online world is full of risks. Our report on cyber threats in Southern Africa is key for anyone wanting to protect their...
Google's Response to Pixel Zero-Days: CVE-2024-29745, CVE-2024-29748; ...
Google’s Response to Pixel Zero-Days: CVE-2024-29745, CVE-2024-29748; Chrome V8 Zero-Day, CVE-2024-3159 [Update] April 5, 2024: “CISA Urges Immediate Action on Pixel Zero-Day Vulnerabilities” Google ...

Critical OS Command Injection Flaw in Progress Flowmon: CVE-2024-2389
Critical OS Command Injection Flaw in Progress Flowmon: CVE-2024-2389 Progress disclosed a highly critical vulnerability, CVE-2024-2389, that affects the Flowmon product. Exploiting this vulnerability...

The Anatomy of Stealers: How Are They Stealing Our Information? Where ...
The Anatomy of Stealers: How Are They Stealing Our Information? Where Are They Taking It? The world of cyber security faces new and more complex threats every day. Among these threats, which we encoun...

How to Detect & Prevent Ransomware Attacks (2024 CISO Edition)
How to Detect & Prevent Ransomware Attacks (2024 CISO Edition) ...

What Do You Need to Know About the Linux XZ Utils Vulnerability, CVE-2...
What Do You Need to Know About the Linux XZ Utils Vulnerability, CVE-2024-3094? A researcher has identified a critical vulnerability in Linux’s XZ Utils, a command line tool for XZ format compression....

U.S. Faces Cyber Onslaught: Fico Breach, ID, CC, Military Data Sale
U.S. Faces Cyber Onslaught: Fico Breach, ID, CC, Military Data Sale Explore the latest dark web threats uncovered by SOCRadar’s Dark Web Team. From breaches affecting major corporations such as Fico t...

Top 10 Cybersecurity Books
Top 10 Cybersecurity Books With new threats and challenges emerging every day within the cybersecurity field, to stay ahead of the curve, it’s necessary to keep learning. One of the best ways to do th...

Inevitable Tool in Pentesters’ Arsenal: Password Dictionary Lists
Inevitable Tool in Pentesters’ Arsenal: Password Dictionary Lists Newbie penetration testers often struggle to grasp the significance of the initial findings reported by most Dynamic Application Scann...



































