
Dark Web Profile: DonutLeaks
In 2022, the DonutLeaks group emerged as a significant player, demonstrating a sophisticated approach to data extortion. Linked to cyber incidents targeting notable enterprises such as Greek natural gas company DESFA, UK architectural firm Sheppard Robson, and multinational construction company Sando, DonutLeaks has swiftly garnered attention for its aggressive tactics and extensive data leaks when it first emerged. The group’s evolution from an affiliate-based association with established threat groups to developing its own customized ransomware marks a pivotal moment in the cybersecurity landscape.

DonutLeaks’ logo in their main page, seems like AI generated text is not working.
Who is DonutLeaks?
DonutLeaks, initially identified in August 2022, has quickly made its mark through double-extortion attacks on enterprises. This group was allegedly associated with prominent threat groups like Hive and Ragnar Locker, indicating a nexus of affiliations within the cybercriminal ecosystem. Later, DonutLeaks unveiled its own encryptor, showcasing a move towards independence and a desire to monetize data more effectively. The group’s ransom notes are characterized by intriguing graphics and humorous content, reflecting a blend of technical prowess and psychological manipulation in their extortion tactics.
However, the group’s latest activities do not contain any ransomware or encryption, which is in line with the latest trend. Threat actors not dealing with ransomware resort to data extortion and share sensitive data on data leak sites. While this may seem less benign initially, it results in much more targeting of institutions containing sensitive data. They threaten many critical industries, especially Healthcare.

About one of their latest victims, a Healthcare company’s alleged data has been published, nothing about encryption or ransomware was mentioned.
Relations and Modus Operandi
A post by BleepingComputer shed light on DonutLeaks’ advancements when they first emerged. They have uncovered new samples of an encryptor used by the group, confirming its utilization in attacks. This customized ransomware, upon execution, selectively encrypts files with specific extensions while avoiding critical system files and directories. Encrypted files bear the distinct “.d0nut” extension, a signature of Donut Leaks’ operations.
This is how we see that traces of ransomware appear in these attacks, which were reported by their victims when they first emerged, but we also said that they are not dealing with ransomware anymore. Extortion only for now.
DonutLeaks made their ransom notes more interesting by using creative designs. They hide their messages using special techniques, like encoding and JavaScript. Some notes even have funny pictures, like a spinning donut made of text. They also pretend to show error messages on a computer screen, followed by a message asking for money. These tricks show how DonutLeaks tries to be unique among other ransomware groups. We can say that they no longer share ransom notes, but similar themes are still present on data leak sites.
Apart from the encryptor, DonutLeaks made a tool to create programs with a TOR client inside. This tool helps them reach their data leak sites better, making their extortion work more effective.
An identifier generator is still working on their leak sites
One interesting thing about the group is DonutLeaks’ journey is intertwined with several notable ransomware groups, including Ragnar Locker and Hive. The group’s involvement in attacks on DESFA, Sheppard Robson, and Sando underscored its collaborative or maybe affiliate-based approach within the cybercriminal landscape, because the same attacks are also listed in other leak sites. BleepingComputer reported at that time that DonutLeaks’ data leak site hosted more extensive data compared to other ransomware sites, hinting at its more significant role in these attacks.
Therefore, it can be claimed that the group, in addition to being associated with other ransomware groups, was a direct affiliate and later turned into its own ransomware operation. However, this group, which is only making extortion by 2024, may have been affected by the dismantlement of the mentioned ransomware groups and cannot receive support from them.
However, the fact that this group, which once had the cortion is more profitable in the labor-performance relationship, or it mayapacity to craft its own ransomware strains, is currently only extorting may indicate that ext also indicate that more skilled actors within the group are no longer involved.
Dispute with Monti
In 2023, the MONTI ransomware group added DonutLeaks to their leak site. The message accompanying this listing suggests a financial dispute, claiming that DonutLeaks “stole 100,000 USD and didn’t fulfill the terms of the deal.” Intriguingly, the listing includes alleged login credentials for DonutLeaks’ admin cPanel.
Current panel for login
However, the credentials on _D#NUT:ch(data leak site’s login panel), they were found to be non-functional. This discrepancy raises questions about the accuracy of MONTI’s claims and the authenticity of the provided login details. It’s plausible that Donut Leaks may have preemptively changed their login credentials in response to this public disclosure.
The login screen for DonutLeaks carries a message urging caution against hijacking, cracking, hacking, and other illicit activities, emphasizing the group’s stance on maintaining security and integrity.
The situation prompts speculation about a potential fallout between Donut Leaks and MONTI, possibly stemming from a business deal gone awry. MONTI’s description of Donut Leaks as “gay rippers” adds a layer of intrigue to the unfolding narrative.
Donut Leaks’ Response to MONTI’s Accusations
In response to MONTI’s accusations, Donut Leaks provided a detailed statement. The group clarified that all TOR services are securely managed within isolated docker containers, ensuring the integrity and security of their operations. They refuted the claim of owing 100,000 USD to MONTI, emphasizing their commitment to upholding agreements and maintaining their reputation.
Donut Leaks underscored their focus on quality over quantity, highlighting the rigorous security measures in place to safeguard their software and data. They expressed confidence in their encryption practices and backup protocols, dismissing any allegations of breaching agreements or compromising sensitive information.
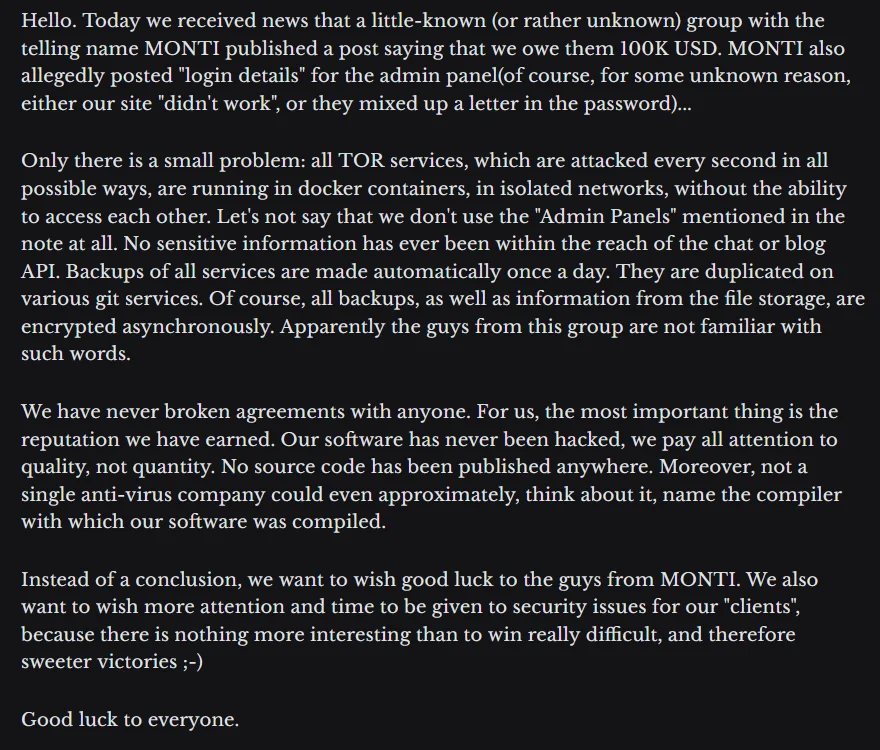
About MONTI’s claim
The incident did not escalate elsewhere after that, but DonutLeaks appears to have had enemies in the ransomware landscape; DDoS protection on their sites is perhaps still active in this context. More interestingly, DonutLeaks later listed another group, INC Ransomware, as a victim and accused it of listing the data they shared.
So, these events went down in history as incidents that showed how interconnected the ransomware landscape can be, especially in the Russian cybercrime world. Monti was a Conti-based ransomware operation, they targeted DonutLeaks, and DonutLeaks was probably an affiliate of Hive and Ragnar Locker, and later spun off into a more singular operation. INC Ransomware was another group, possibly a Russian-related ransomware operation, also clashed with DonutLeaks.
Victimology
Donut Leaks has left a significant impact on a wide range of victims across various countries and industries, showcasing the global reach and diversity of its targets. The victims span multiple sectors, including technology, healthcare, architecture, government, legal services, travel, and more. These attacks have affected organizations in different countries, highlighting the international scope of Donut Leaks’ operations.

Index page of DonutLeaks
The group shares its victims on the data leak site and displays the victims whose data it publishes in the index section, ready for download. As always, the US remains one of the main targets, but no other country specifically stands out. However, in an industrial sense, Healthcare stands out because it contains seriously sensitive data.
We can even observe the group’s reversion to extortion-only attacks by examining nearly 30 of its victims. When it first emerged, sectors such as Manufacturing were at the forefront, but recently Healthcare is dominant.
Mitigation Strategy: Data Protection Focus
In light of the evolving tactics employed by DonutLeaks and their focus on data exfiltration and extortion, organizations must adopt a robust mitigation strategy centered around data protection. Here’s a comprehensive approach to mitigate the risks posed by DonutLeaks and similar threat actors.
Data Classification and Encryption:
Develop and enforce data classification policies to identify and categorize sensitive information, such as customer data, financial records, and intellectual property.
Encrypt sensitive data both at rest and in transit using strong encryption algorithms to prevent unauthorized access and protect against data theft.
Access Control and Principle of Least Privilege (PoLP):
Implement stringent access controls to restrict data access based on the principle of least privilege, ensuring that employees only have access to data essential for their roles.
Regularly review and update access permissions to minimize the risk of insider threats and unauthorized access to sensitive data.
Network Segmentation and Monitoring:
Segment networks to create isolated zones and limit the spread of potential breaches, reducing the impact of a successful attack.
Deploy robust network monitoring tools, such as Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) solutions, to detect and respond to suspicious activities indicative of data exfiltration attempts.
Employee Training and Awareness:
Conduct regular cybersecurity training sessions to educate employees about phishing attacks, social engineering tactics, and the importance of data protection.
Foster a culture of security awareness where employees are encouraged to report suspicious activities promptly and follow best practices for data security.
Incident Response Plan:
Develop a comprehensive incident response plan specifically tailored to address data breaches and extortion attempts by threat actors like DonutLeaks.
Define clear protocols for incident escalation, communication procedures, legal considerations, and coordination with law enforcement agencies.
Backup and Recovery:
Implement a reliable backup and recovery strategy to ensure data availability and continuity in the event of a ransomware attack or data breach.
Regularly test backup systems to verify their effectiveness in restoring critical data and minimizing downtime.
Vendor and Third-Party Risk Management:
Evaluate the security posture of vendors and third-party partners who have access to sensitive data, ensuring they adhere to strict security standards and undergo regular security assessments.
Establish contractual agreements that include security requirements and responsibilities to mitigate third-party risks effectively.
By implementing these proactive measures, organizations can strengthen their defenses against data extortion threats posed by groups like DonutLeaks. Regular monitoring, testing, and refinement of these strategies are essential to adapt to evolving cyber threats and protect sensitive data effectively.
SOCRadar: Enhancing Data Breach Detection and Mitigation
SOCRadar presents an indispensable solution for detecting and addressing data leaks and credential compromises, bolstering your organization’s resilience against cyber threats. Through continuous monitoring of both surface and dark web sources, SOCRadar swiftly detects any exposure of sensitive information, including employee emails, customer login credentials, and financial data such as credit card numbers.
Key Use Cases of SOCRadar in Data Breach Scenarios:
Early Threat Detection: SOCRadar enables early detection of potential data breaches by actively scanning web sources for any signs of compromised data or unauthorized access attempts.
Real-time Alerting: The platform provides real-time alerts and notifications for critical security incidents, allowing your security team to respond promptly and mitigate risks effectively.
Threat Intelligence: SOCRadar offers comprehensive threat intelligence, including contextual information about threat actors, attack vectors, and potential impact, empowering your organization to make informed decisions and prioritize response efforts.
Intellectual Property Protection: SOCRadar safeguards your intellectual property by monitoring for unauthorized access or exposure, preventing data theft and preserving the integrity of your proprietary information.
Resource Optimization: Through intelligent prioritization of security incidents, SOCRadar helps your team allocate resources efficiently, focusing on critical areas that require immediate attention and mitigation.
In summary, SOCRadar’s advanced capabilities in threat detection, real-time alerting, threat intelligence, compliance support, and resource optimization make it a crucial ally in fortifying your organization’s defenses against data extortion teams like Meow and other cyber threats.




































