
Top 10 RCE Vulnerabilities Exploited in 2023
Cybersecurity unfolds in a continuous interplay between defenders and threat actors – an ever-evolving quest for software vulnerabilities, with both parties engaged in a strategic game of anticipating each other’s next move. One significant category in this landscape is Remote Code Execution (RCE), a subset of Arbitrary Code Execution (ACE) vulnerabilities.
RCE vulnerabilities serve as a common denominator, granting malicious actors the ability to take control of remote machines through code execution across various networks such as LAN, WAN, or the Internet. A remote code execution attack can manifest in various ways, typically involving the injection and activation of code on a target system.
In this article, we will explore the top vulnerabilities that fueled RCE exploits during the year of 2023, dissecting the targets chosen by threat actors and the specific weaknesses they scrutinized and exploited to achieve remote control over systems and networks.
The Mechanism of Remote Code Execution (RCE) Attacks
A closer look at the anatomy of an RCE attack reveals a strategic exploitation of vulnerabilities that grant unauthorized control over remote systems.
The attack vector could be diverse, with attackers exploiting various loopholes to infiltrate and manipulate systems. One prevalent avenue is through lax input validation in websites or applications, providing an entry point for unintended server behaviors and the execution of arbitrary code.
Consider the risks posed when user input is accepted without proper security measures – a scenario where cyber adversaries find the door wide open for injecting malicious code into systems. Likewise, if a widely used component is exposed to the Internet or is outdated, even with internal incident response procedures in place, it could hurl organizations into compromise.
RCE threats extend their reach to authentication and session management features. Attackers, exploiting weaknesses in these areas, can compromise sensitive information like passwords or keys. The absence of proper verification mechanisms for user input becomes a breeding ground for executing valid code on the target machine. Malicious actors leverage dynamic code generation to transform seemingly benign inputs into executable code, allowing them to launch a devastating assault on the targeted applications.
In our 2023 review of the CISA KEV catalog, Remote Code Execution (RCE) vulnerabilities dropped to the second rank, trailing behind Privilege Escalation vulnerabilities, in contrast to their overwhelming dominance on the list in 2022. Nonetheless, RCE threats maintain a robust position, representing one of the most formidable and feared threats in the cybersecurity landscape.
Now, with a better understanding on RCE attacks, let’s delve into the specific vulnerabilities that threat actors strategically exploited in 2023 to achieve remote capabilities.
1 – CVE-2023-26360 (CVSS: 9.8), Adobe ColdFusion
In the cybersecurity landscape of 2023, one prominent vulnerability that sent shockwaves across organizations was CVE-2023-26360 within Adobe ColdFusion. This vulnerability stemmed from a deserialization flaw in handling untrusted data, opening a gateway for remote code execution.
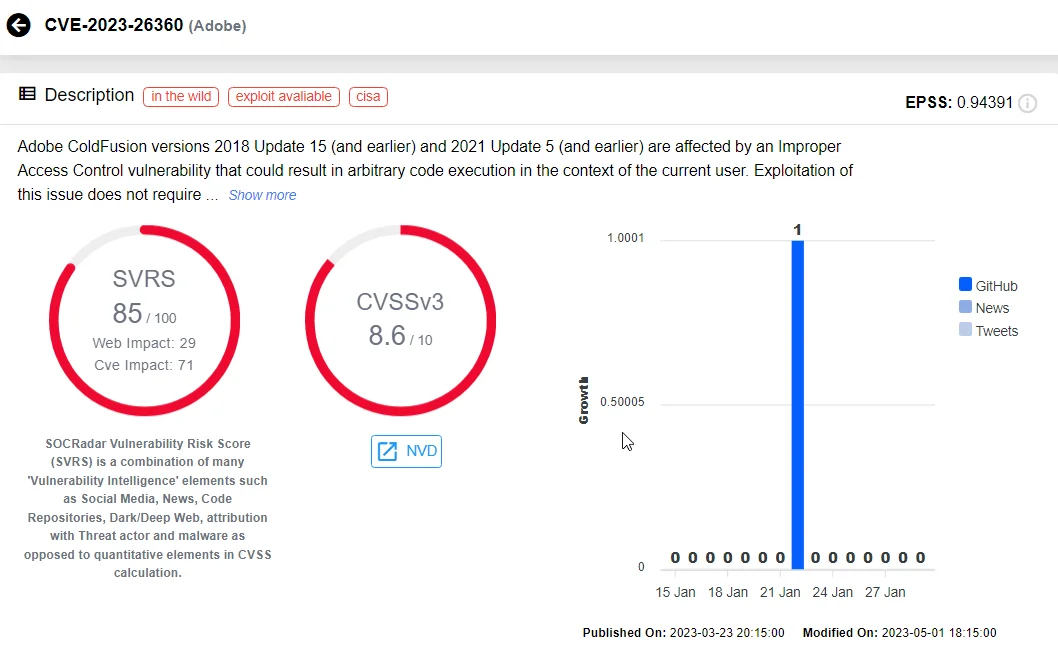
CVE-2023-26360 on SOCRadar Vulnerability Intelligence
In December 2023, CISA sounded the alarm, revealing that threat actors, still unidentified, had effectively exploited this vulnerability to target a Federal Civilian Executive Branch (FCEB) agency.
The aftermath of investigations painted a worrisome picture – network logs disclosed a compromise spanning June to July 2023, with at least two public-facing servers falling victim to the exploitation.
The attackers, using CVE-2023-26360, managed to establish a firm foothold on the targeted agency’s systems. Their modus operandi included issuing commands on web servers and deploying malware to further solidify their grip. Their primary focus was reconnaissance – a meticulous mapping of their victim’s network.
On the other hand, there was no discernible evidence of successful data exfiltration or lateral movement, leaving the extent of the breach confined to the initial compromise.
2 – CVE-2023-3519 (CVSS: 9.8), Citrix NetScaler ADC and NetScaler Gateway
CVE-2023-3519 affected Citrix NetScaler ADC and NetScaler Gateway with a staggering CVSS score of 9.8. This vulnerability unfolded as a code injection flaw, allowing unauthenticated remote code execution without the need for any privilege or user interaction, and could result in substantial damage.
The gravity of CVE-2023-3519 became palpable when, merely two weeks after the reservation of its CVE code, the first Proof of Concepts (PoCs) began to surface. The ominous date of July 19, 2023, marked the emergence of these initial PoCs on our radar.
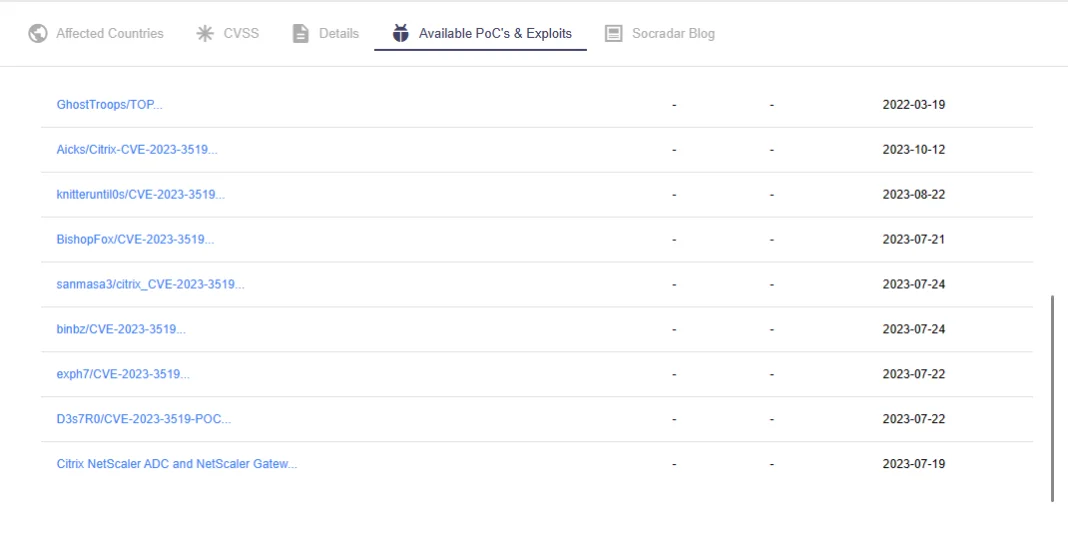
POCs & exploits of CVE-2023-3519 on SOCRadar Vulnerability Intelligence
Compounding the urgency, a revelation on the dark web, predating the official announcement by Citrix on July 18, 2023, hinted at the sale of an exploit targeting a remote code execution vulnerability associated with Citrix, possibly alluding to this specific vulnerability.
The ominous role of the FIN8 hacking group came into focus in late August 2023, with researchers attributing them to the active exploitation of CVE-2023-3519. The attacks bore striking similarities to previous instances, indicating a ransomware attack orchestrated by FIN8.
October 2023 brought further revelations as IBM’s X-Force reported a credential theft campaign, discovered in September, targeting Citrix NetScaler Gateway instances vulnerable to CVE-2023-3519. The threat actors, registering multiple domains in August and leveraging Cloudflare to obfuscate their hosting location, affected about 600 unique victim IP addresses. According to IBM, the campaign likely commenced on August 4, coinciding with the registration of the domains, while infections began around August 11.
3 – CVE-2023-36884 (CVSS: 8.8), Microsoft Windows
CVE-2023-36884 is marked as a zero-day vulnerability, initially disclosed in the July 2023 Patch Tuesday by Microsoft.
Originally perceived as a remote code execution vulnerability, the situation took an intriguing turn when it was addressed during Microsoft’s August 2023 Patch Tuesday, and the flaw was reclassified as a security feature bypass. The intricate nature of this vulnerability involved the exploitation of Microsoft Office and its defense mechanisms.
This high-severity vulnerability specifically targeted Microsoft Windows Search, rooting from an unspecified flaw that, when exploited, allowed an attacker to bypass Mark of the Web (MOTW) defenses using a specially crafted Microsoft Office document. The consequence was a pathway to remote code execution, presenting a serious threat to system integrity.
The vulnerability, CVE-2023-36884, was actively exploited to distribute the RomCom malware.
4 – CVE-2023-24489 (CVSS: 9.8), Citrix Content Collaboration
CVE-2023-24489, a vulnerability scoring an alarming 9.8 on the CVSS scale, affected Citrix Content Collaboration’s ShareFile application.
ShareFile, the cloud-based file sharing application in question, harbored a cryptographic flaw in its Storage Zones Controller, a .NET web application operating under IIS. Thereby, the vulnerability, CVE-2023-24489, became an avenue for exploitation, offering threat actors the capability to execute unauthorized file uploads and wield remote code execution.
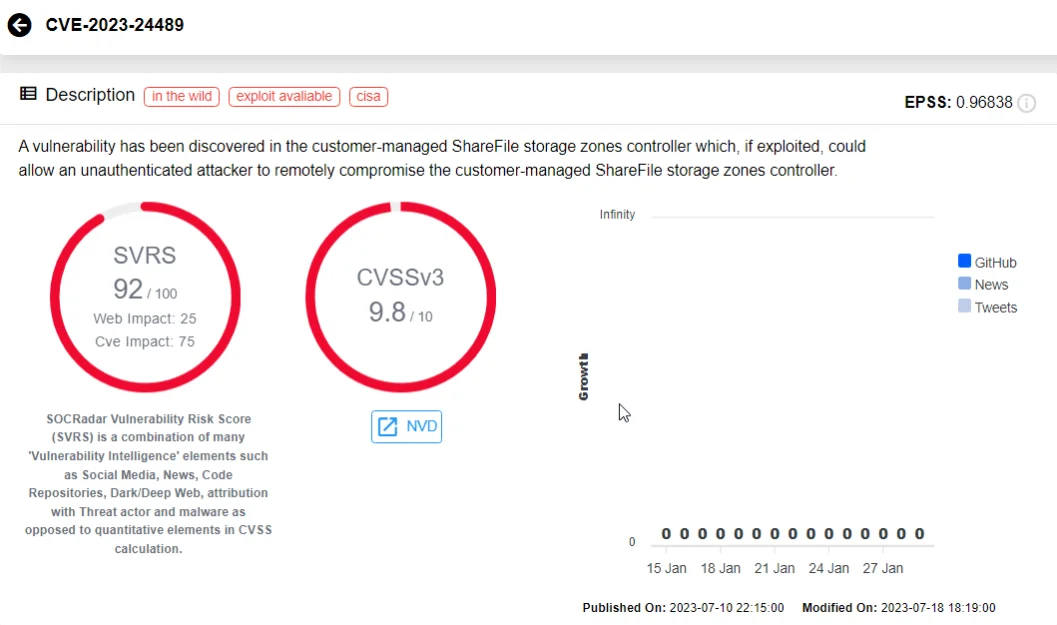
CVE-2023-24489 on SOCRadar Vulnerability Intelligence
Researchers ventured into exploiting this vulnerability, successfully gaining unauthorized access and control, while August 2023 witnessed the initial warning signs when Greynoise flagged the first real attempts to exploit CVE-2023-24489. Suspicious IPs were observed attempting to exploit the vulnerability, taking advantage of the application’s handling of cryptographic operations to achieve unauthenticated arbitrary file upload and remote code execution.
The gravity of the situation heightened when, in mid-August, CISA added this vulnerability to its Known Exploited Vulnerabilities (KEV) list, citing active targeting by unknown actors. The agency, in its warning, emphasized that such vulnerabilities were common vectors in data theft attacks.
The aftermath of CISA’s alert saw a surge in exploitation attempts, attributed to the rapid development of exploits by threat actors and the sharing of exploits on public repositories like GitHub by researchers.
5 – CVE-2023-27997 (CVSS: 9.8), Fortinet FortiGate SSL-VPN
CVE-2023-27997 is a heap-based buffer overflow vulnerability in Fortinet’s FortiGate SSL VPN appliances, allowing an unauthenticated, remote attacker to execute code or commands through specially crafted requests.
Exploiting CVE-2023-27997, a threat actor can bypass authentication mechanisms and achieve RCE. Even in environments where Multi-Factor Authentication (MFA) was enabled, this vulnerability still posed a risk.
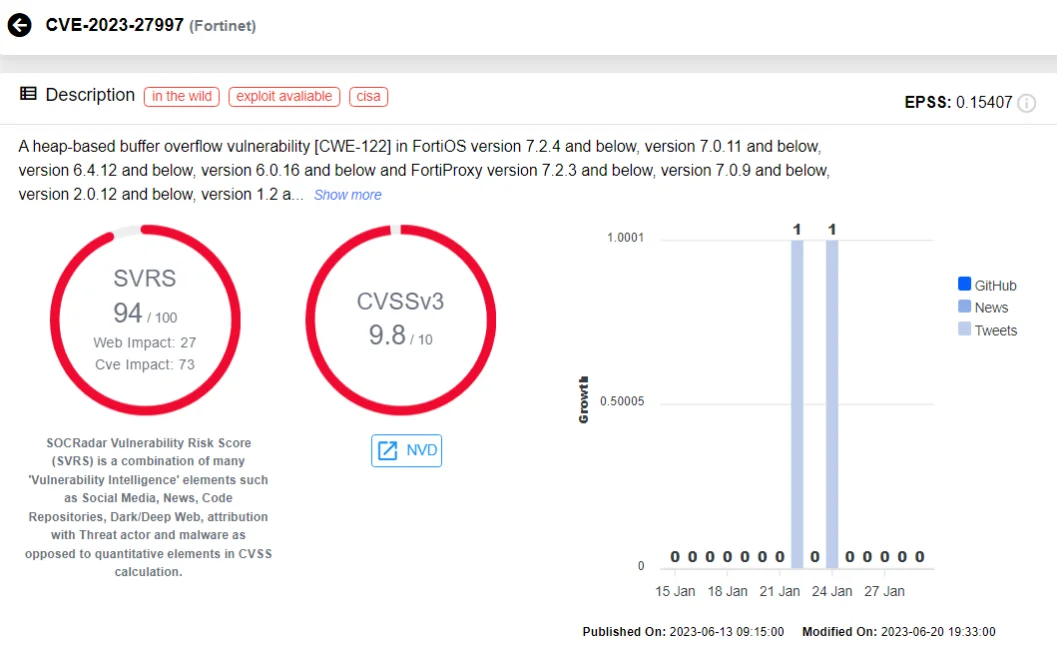
CVE-2023-27997 on SOCRadar Vulnerability Intelligence
Fortinet released a patch for this vulnerability in June 2023, before its disclosure, allowing customers ample time to update their SSL VPN appliances and fortify their defenses against potential exploits.
Despite the proactive approach from Fortinet, the widespread usage of Fortinet devices make them attractive targets for cyber adversaries. FortiGate firewalls, being among the most popular firewall and VPN devices in the market, are bound to be targeted by malicious actors.
By July 2023, many FortiGate firewalls remained susceptible to the vulnerability – to this day, the Shodan results show a consistent presence of exposed devices.
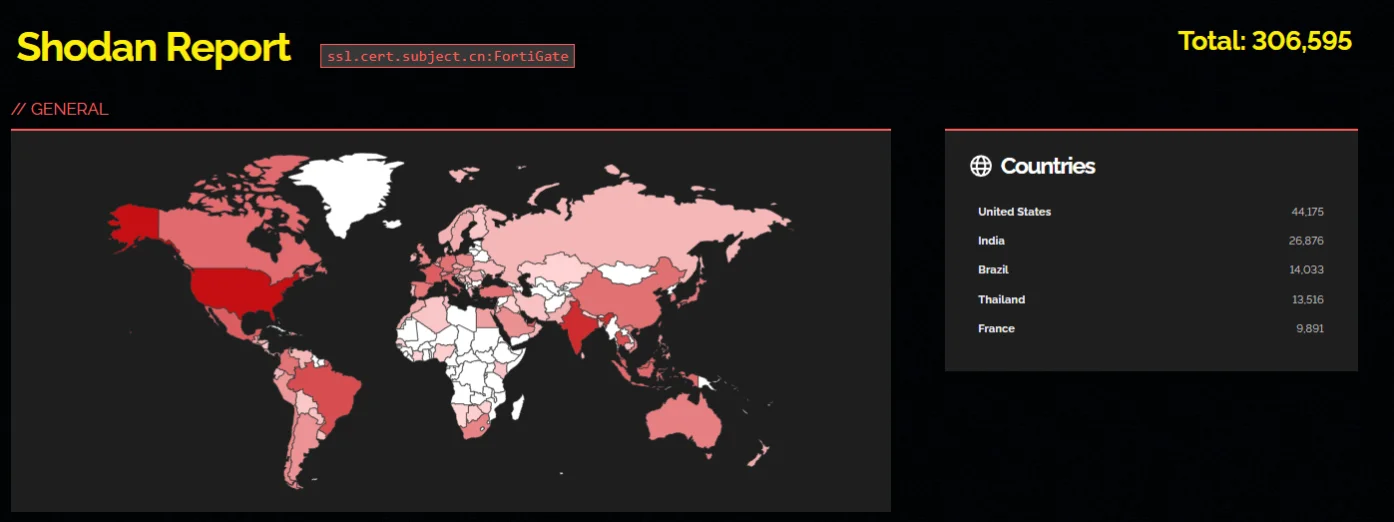
Exposed FortiGate devices (Shodan)
6 – CVE-2023-20887 (CVSS: 9.8), VMware Aria Operations for Networks
CVE-2023-20887, a critical vulnerability within VMware Aria Operations for Networks (formerly vRealize Network Insight), is a command injection issue that could be exploited by a malicious actor with network access, leading to remote code execution.
CVE-2023-20887 on SOCRadar Vulnerability Intelligence
The low-complexity nature of the vulnerability heightened the risk, as threat actors could exploit the vulnerability with relative ease, without the need for user interaction. The implications of a successful exploit were severe – a malicious actor, armed with network access to VMware Aria Operations for Networks, could execute arbitrary code remotely, potentially wreaking havoc on the targeted system.
VMware had to revise the initial advisory within a month of the vulnerability’s disclosure because threat actors had started actively exploiting it in the wild. Proof-of-Concept (PoC) exploit codes for the vulnerability became available within the same timeframe, further exacerbating the risk landscape.
7 – CVE-2023-33009 and CVE-2023-33010 (CVSS: 9.8), Zyxel
Zyxel ATP, USG FLEX, USG FLEX 50(W), USG20(W)-VPN, VPN, and ZyWALL/USG firewalls faced critical vulnerabilities, labeled as CVE-2023-33009 and CVE-2023-33010.
These vulnerabilities manifested as buffer overflow issues, impacting the notification function and ID processing function, respectively. Unauthenticated attackers could exploit these vulnerabilities, enabling them to cause Denial-of-Service (DoS) and execute remote code on Zyxel firewall devices.
CVE-2023-33009 on SOCRadar Vulnerability Intelligence
Both CVE-2023-33009 and CVE-2023-33010 were actively exploited, leading to their inclusion in CISA’s Known Exploited Vulnerabilities (KEV) catalog in June 2023.
Simultaneously, another Zyxel vulnerability, CVE-2023-28771, facilitated remote unauthenticated command injection and was actively exploited by threat actors in botnet attacks. Zyxel firewalls, facing the same fate with FortiGate firewalls due to their widespread use, are appealing targets for threat actors.
8 – CVE-2023-0669 (CVSS: 7.2), Fortra GoAnywhere MFT
This pre-auth remote code execution vulnerability resides in the License Response Servlet component of Fortra’s GoAnywhere MFT (Managed File Transfer), where an attacker can exploit the deserialization of a controlled object.
The successful exploitation of CVE-2023-0669 grants malicious actors the ability to execute code remotely; initial signs of suspicious activity related to this zero-day vulnerability were detected on January 18, 2023, while it was officially disclosed by Fortra on February 1, 2023.
CVE-2023-0669 on SOCRadar Vulnerability Intelligence
It is noteworthy that this vulnerability can only be exploited by gaining access to the application’s administrative console. Typically restricted to a private company network, access may be granted through VPN or specific IP addresses in an allow list. Despite these limitations, after the disclosure of this zero-day remote code execution vulnerability in Fortra GoAnywhere MFT, malicious actors actively attempted to exploit it.
The Department of Health and Human Services (HHS) Cybersecurity Coordination Center issued a caution to healthcare providers in the U.S., highlighting ransomware attacks executed by known groups in early 2023, using CVE-2023-0669.
The GoAnywhere MFT RCE vulnerability has been exploited by notorious ransomware groups such as LockBit, Cl0p, and BlackCat (ALPHV), which contributed to a staggering 91% increase in ransomware attacks within a month.
9 – CVE-2023-37450 (CVSS: 8.8), Apple
CVE-2023-37450 is a zero-day vulnerability that impacted Apple devices, residing in the WebKit engine that powers Apple’s web browsers. This vulnerability allows attackers to execute arbitrary code on targeted devices by luring users to visit malicious websites.
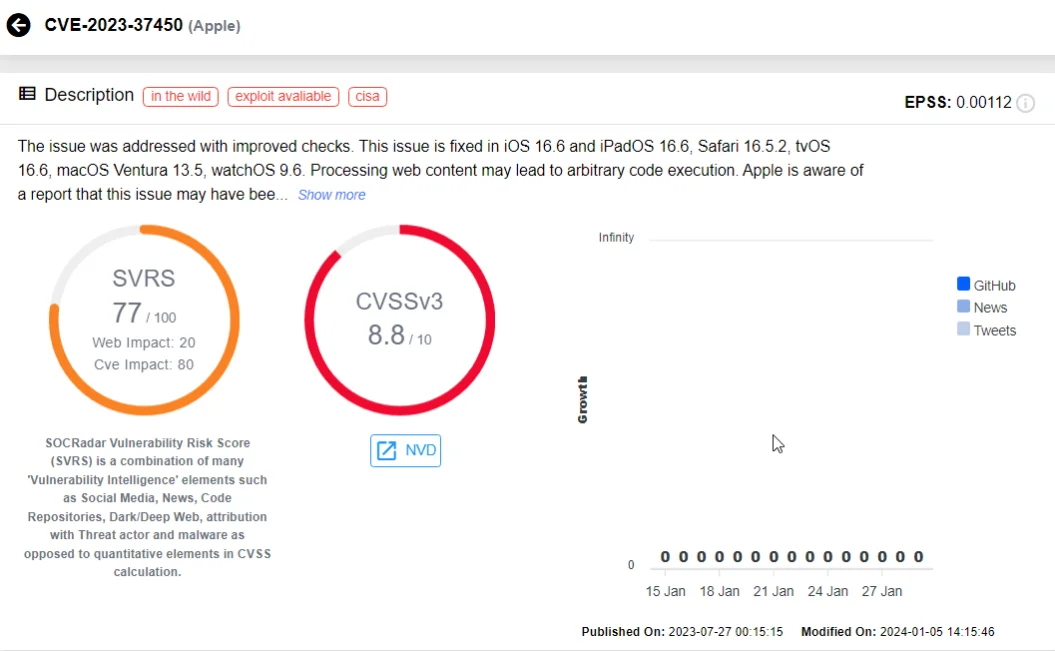
CVE-2023-37450 on SOCRadar Vulnerability Intelligence
CVE-2023-37450 is part of a broader trend, with several other Apple vulnerabilities related to the WebKit engine, stemming from various issues like type confusion, out-of-bounds read, use-after-free, and out-of-bounds write, making the list of most exploited vulnerabilities in 2023 that lead to RCE. These vulnerabilities are assigned the following CVE identifiers: CVE-2023-23529, CVE-2023-28204, CVE-2023-28205, and CVE-2023-28206.
It is important to recognize the high value placed on Apple zero-day vulnerabilities. These vulnerabilities, sought by both attackers or researchers, carry substantial worth, evident in bounty programs offering rewards ranging from $2,500 to $2,500,000.
10 – CVE-2023-22952 (CVSS: 8.8), SugarCRM
Multiple SugarCRM products faced security challenges due to CVE-2023-22952, a remote code execution vulnerability discovered in the EmailTemplates component. This vulnerability potentially allows for the injection of custom PHP code through the affected component, using a specially crafted request.
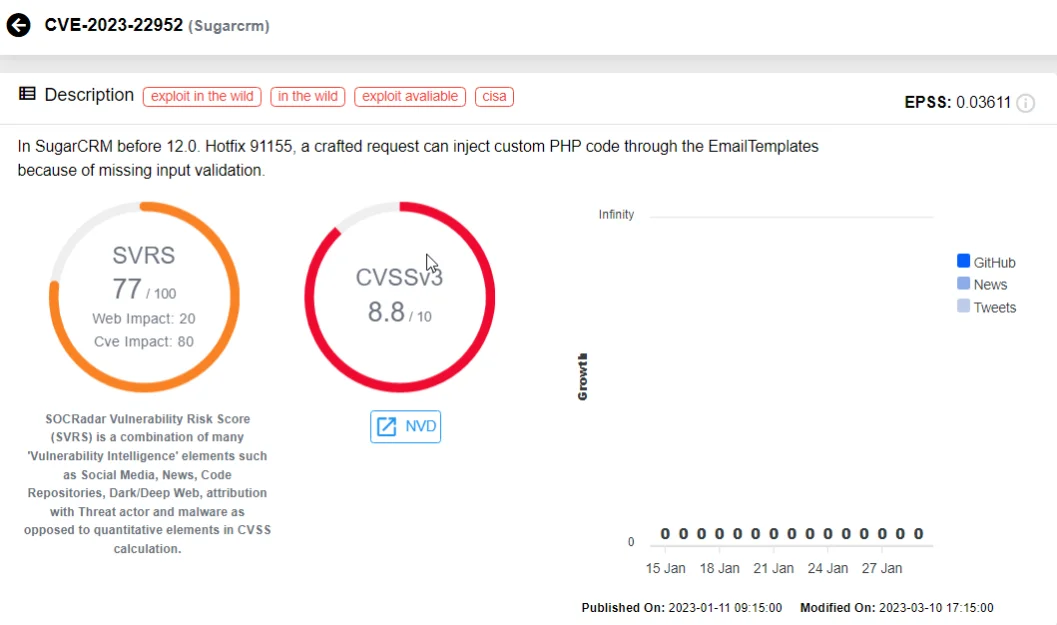
CVE-2023-22952 on SOCRadar Vulnerability Intelligence
Upon investigating the scope of the vulnerability, researchers at Censys identified 3,059 instances of SugarCRM exposed to the internet, with 354 unique IP addresses infected by the webshell related to its exploit, signaling active exploitation of the RCE vulnerability.
A Deeper Look at the Top RCE Vulnerabilities Exploited in 2023
Continued Exploitation Targeting Out-of-Date Instances
The vulnerabilities we have discussed, particularly those affecting widely-used products such as Citrix’s, showcase the persistent challenges organizations face in securing their systems. Despite awareness and patches, threat actors continue to exploit known vulnerabilities by seeking out unpatched instances. Therefore, organizations should promptly identify signs of compromise within their systems and apply updates and security patches promptly for the products they use.
SOCRadar, with its Attack Surface Management (ASM) module, can help monitor vulnerabilities affecting your organization and provide timely alerts on security issues. Through Digital Footprint, you can keep an eye on your online presence and digital assets.
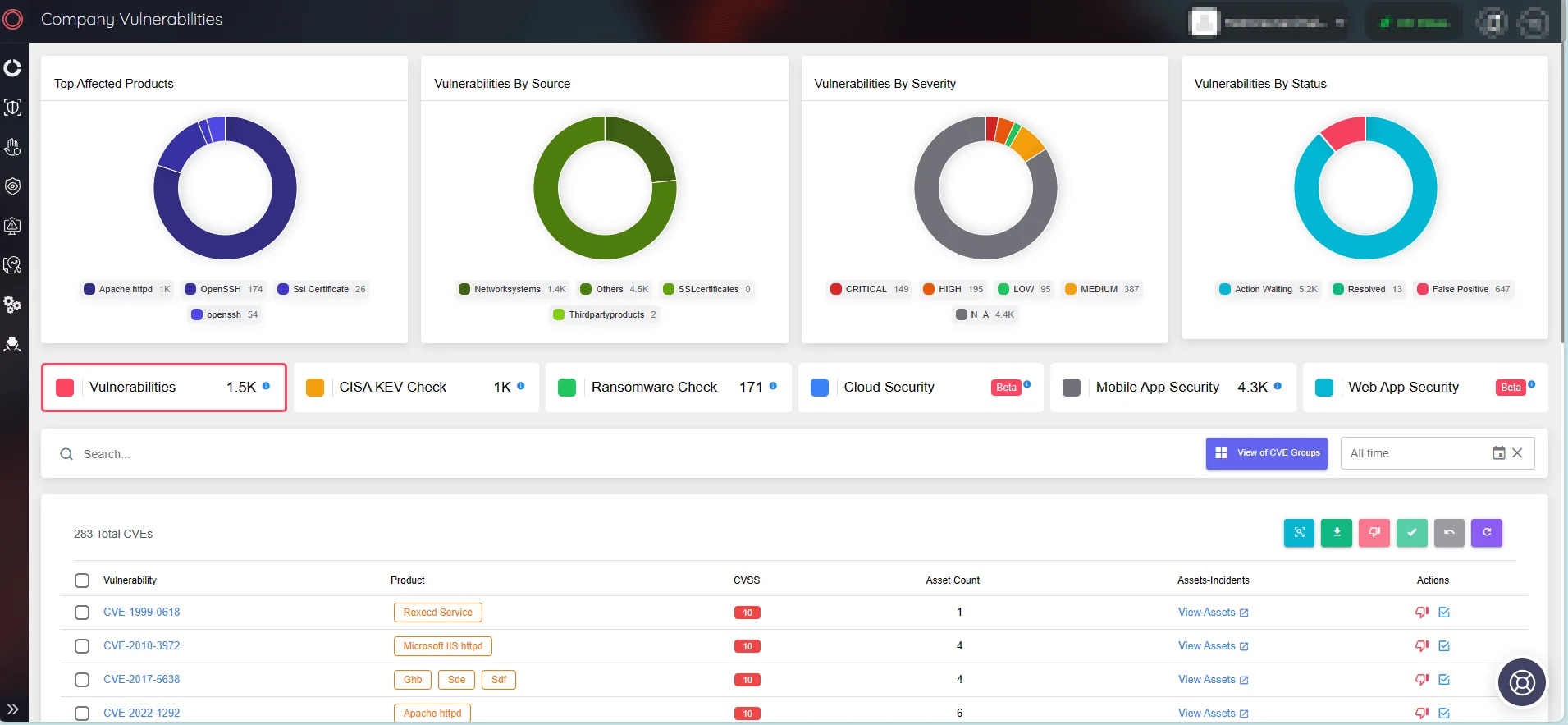
View Company Vulnerabilities via SOCRadar’s ASM
Threat Actors Chasing for New Opportunities
The case of Fortra GoAnywhere MFT (CVE-2023-0669) and the Microsoft Windows (CVE-2023-36884) vulnerabilities set great examples of the rapid exploitation of newly discovered vulnerabilities. These zero-day vulnerabilities expose the immediate risks organizations face when novel vulnerabilities are brought to light. The speed at which threat actors can create successful exploit code and capitalize on such security gaps, compromising valuable assets, underscores the urgency for proactive security measures.
Through SOCRadar’s Vulnerability Intelligence module, you can access information on the latest identified vulnerabilities, including their timeline, exploits, and related repositories. With Vulnerability Intelligence, it is ever easier to track the latest updates and view vulnerability trends. Combining Vulnerability Intelligence and ASM solutions, you can unlock an enhanced approach to vulnerability management.
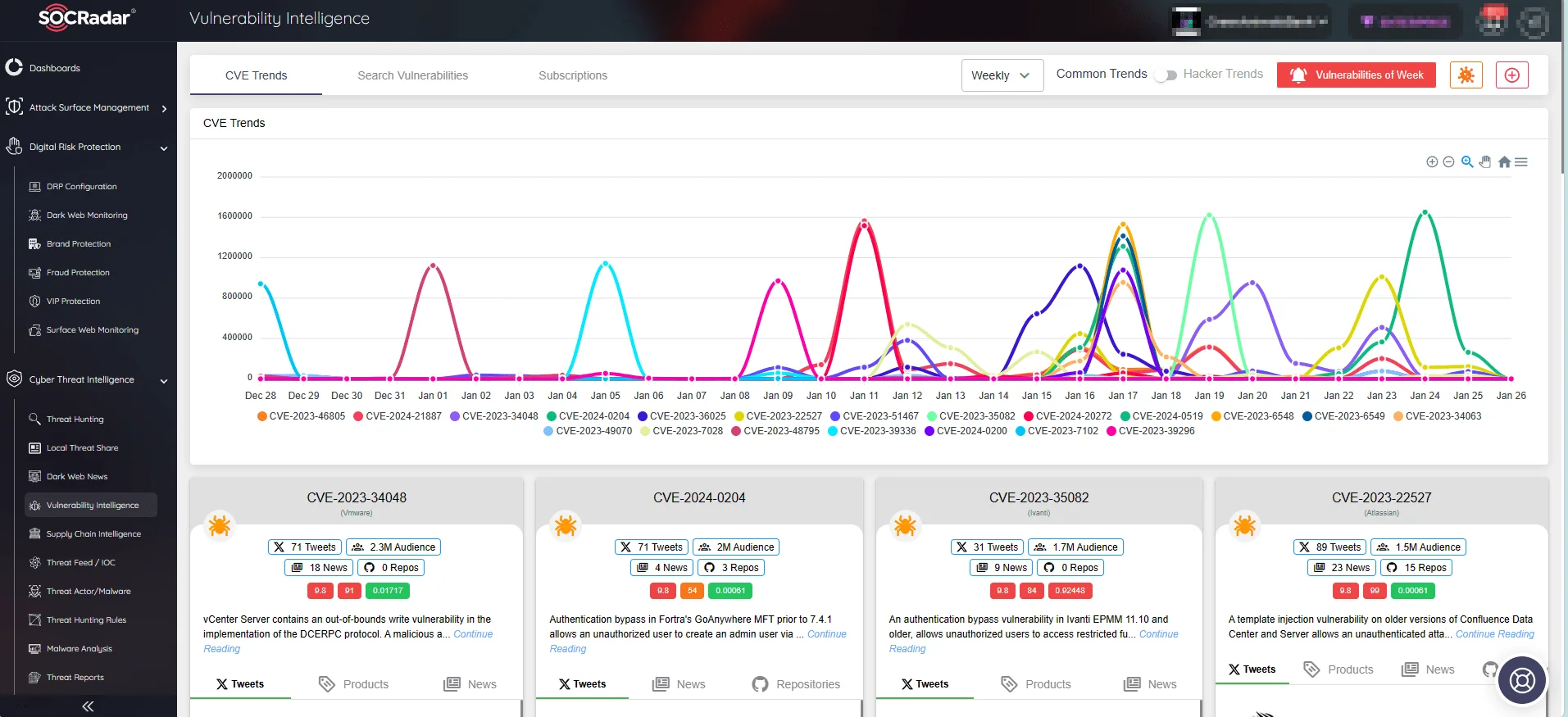
CVE Trends on SOCRadar’s Vulnerability Intelligence
Ransomware Actors Capitalizing on RCE Exploits
Remote Code Execution vulnerabilities can facilitate the initiation of ransomware attacks, exemplified by the exploitation of Fortra GoAnywhere MFT RCE vulnerability. These vulnerabilities serve as gateways for threat actors to gain access, deploy malware, and encrypt systems – or exfiltrate data, depending on their objectives.
The chaos caused by such RCE-enabled ransomware operations highlights the need for robust defense mechanisms to prevent increasingly sophisticated and damaging cyber threats. Staying informed about threat actors’ Tactics, Techniques, and Procedures (TTPs) and activities is one way to boost defenses against these evolving threats.
Moreover, within SOCRadar’s Attack Surface Management module, there is a section to assess whether vulnerabilities impacting your organization have been exploited in ransomware operations. You can navigate to the feature, called “Ransomware Check” under the Company Vulnerabilities page on the platform.
SOCRadar Company Vulnerabilities, Ransomware Check feature
Conclusion
The top vulnerabilities of 2023, outlined in this article, varied widely, yet shared a common thread—they all facilitated Remote Code Execution (RCE) exploits. While no singular vulnerability type perennially demands attention, adopting an effective vulnerability management approach should be our utmost goal, as prioritizing vulnerabilities judiciously optimizes organizational resources and guards against exploitation.
This blog post curated the top vulnerabilities leading to RCE exploits in 2023, presented in reverse chronological order based on a list available here.
As attackers relentlessly evolve their tactics, a dynamic response is required. Reaction post-incident is no longer sufficient; actionable intelligence and automated solutions are pivotal allies in the ongoing battle for digital security. Cyber Threat Intelligence platforms like SOCRadar XTI are invaluable partners, equipping organizations with tools to anticipate, detect, and neutralize threats in real-time.




































