Top 10 Free IoC Search & Enrichment Platforms
Indicators of Compromise (IoCs) are critical pieces of threat intelligence that identify potential breaches in an endpoint or network. These digital assets assist information security professionals in detecting malicious activity or security threats, such as data breaches, insider threats, or malware attacks. Thus, as cybercriminals become more advanced, IoCs constantly change, making detection more difficult.
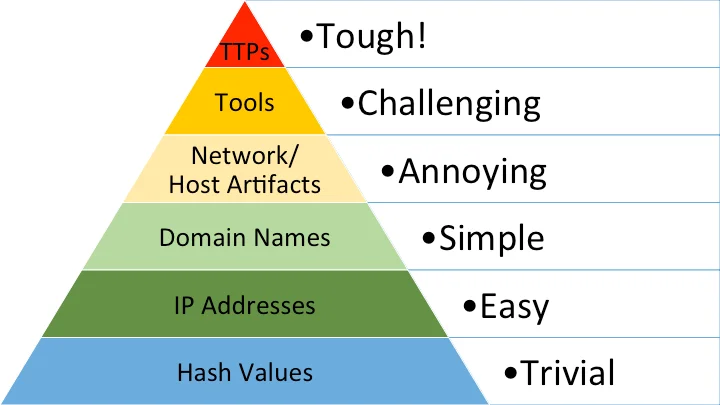
Pyramid of pain, type of indicators (Image)
To help with this effort, several IoC search and enrichment platforms have emerged, each with a unique set of features to improve threat detection and response. These platforms offer real-time, actionable threat intelligence, automated IoC enrichment, and direct integration capabilities, making them valuable resources for organizations looking to improve their cybersecurity posture.
This article will look at the top free IoC search and enrichment platforms that stand out due to their large and active communities, extensive threat data, integration capabilities, and their unique features. However, there is no specific ranking within the top 10 in this article.
1. AlienVault Open Threat Exchange
AlienVault Open Threat Exchange (OTX) is a top threat intelligence platform that offers practical, community-powered threat data. It provides community-generated threat data, offering collaborative research, and automating the update of security infrastructure with threat data from multiple sources.
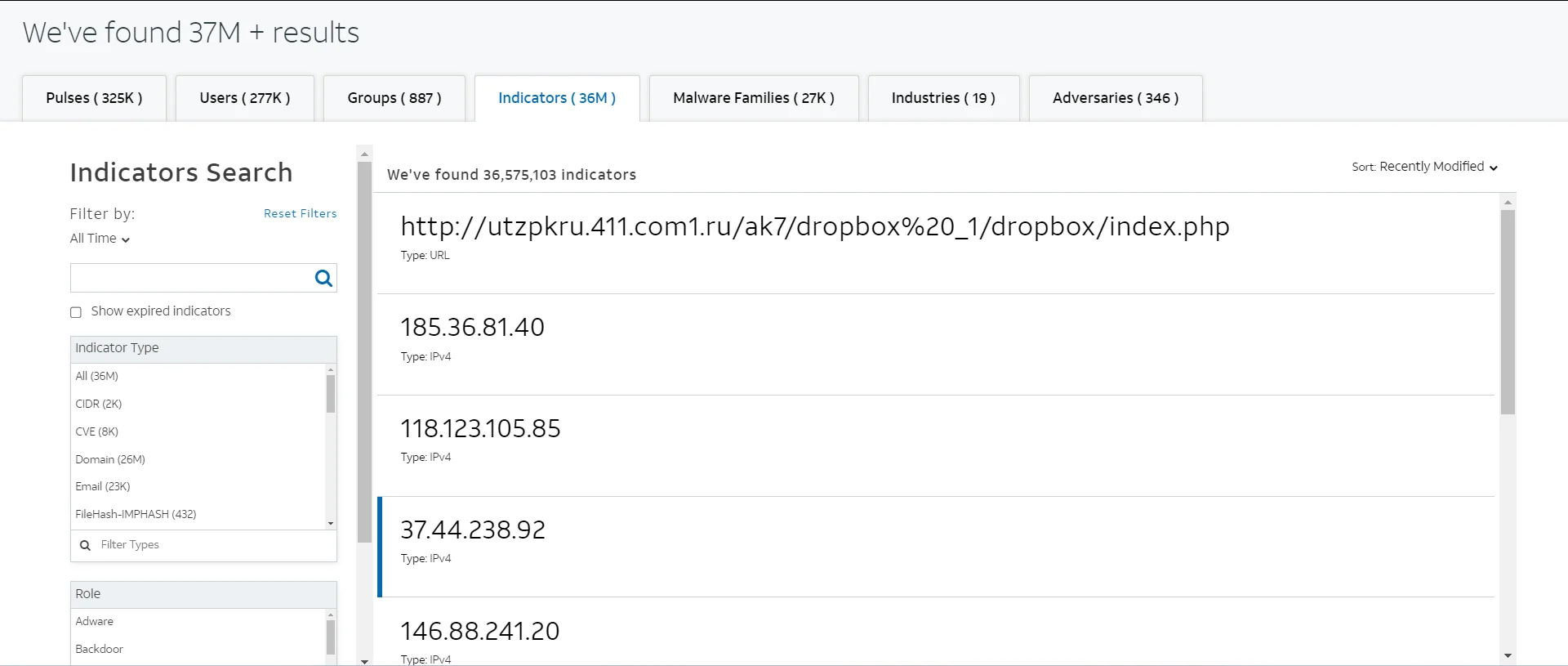
AlienVault Open Threat Exchange Indicators Search
AlienVault OTX’s key features include Pulses, which are the primary means by which the community shares threat information, as well as support for a wide range of Indicators of Compromise (IoCs). The platform promotes active discussion, research, validation, and sharing of the most recent data and trends among the security community. It also provides several methods for security tools to ingest pulse data, allowing for faster and more efficient threat response.
AlienVault OTX provides its participants with real-time, actionable information, allowing them to respond immediately to emerging threats. It processes over 19 million new IoC records per day, providing users with valuable threat intelligence. The platform is known for its user-friendly interface, as well as its large and active community, which shares millions of potential threats on a daily basis.
AlienVault stands out due to its seamless API integration, which is user-friendly. You can utilize the API via the Command Line Interface (CLI) using a traditional approach to integrate with the OTX DirectConnect API with the command below.
curl /api/v1/pulses/subscribed?page=1 -H “X-OTX-API-KEY: <INSERT_USER_API_KEY>”

Popular tool, Suricata is also among the Direct Connection Agents
A use case of integrating AlienVault OTX is with Suricata. This combination should improve network security by allowing Suricata to use OTX’s threat intelligence feeds for more accurate threat detection and automated responses, enhancing overall defense against cyber threats.
For further integration and use cases, check the official website.
2. The IBM X-Force
The IBM X-Force Exchange serves as a cloud-based platform for threat intelligence, enabling users to access, share, and respond to security threats effectively. Users can swiftly analyze global security risks, gather actionable insights, seek expert advice, and collaborate with peers.
Through X-Force, you can establish and oversee a comprehensive security strategy safeguarding your organization against worldwide threats. X-Force offers offensive and defensive services backed by robust threat research, intelligence, and remediation capabilities.
IBM X-Force Exchange
In addition to IBM’s efforts, being a community-driven platform allows searching for up-to-date IoCs on many current threat groups, actors or malware. There is also an API service.
The IBM X-Force Threat Intelligence API enables users to automate the retrieval of threat intelligence data from IBM X-Force Exchange, which is IBM’s cloud-based platform for sharing threat intelligence. This API grants access to categorized IP and URL feeds, detailed IP and URL reports, vulnerability feeds, and all TAXII feeds.
However, IBM’s API integration is available for a fee and includes different versions. If you are still interested, the standard version has a free trial offer.

X-Force Threat Intelligence Standard version has a 30-day free trial
3. Pulsedive
Pulsedive acquires millions of IPs, domains, and URLs from numerous global feeds and user submissions. The active user community contributes new IoCs regularly, providing Pulsedive with unique data. Each indicator undergoes thorough scanning and enrichment by Pulsedive, resulting in a rich repository of real-time contextual information.
Users have the option to conduct active or passive scans on IoCs without necessarily storing them in our database permanently. Pulsedive retrieves data as usual, but if it encounters a new IOC, no data is retained unless explicitly submitted.
This feature is ideal for users who prefer not to share IoCs or are unable to do so. However, it encourages users to contribute when appropriate, allowing others to benefit from fresh threat intelligence.
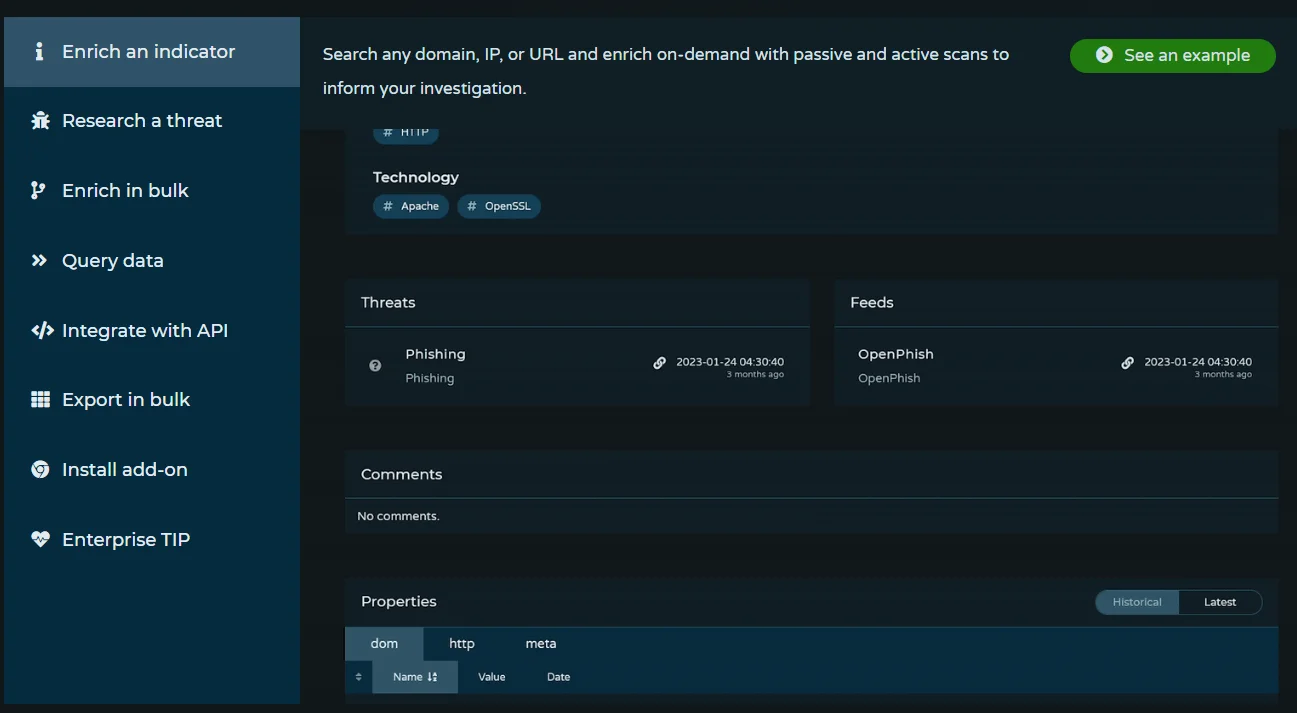
Pulsedive, enriching an indicator
Furthermore, Scans are performed via secondary nodes strategically placed worldwide, safeguarding against direct connections with malicious IoCs.
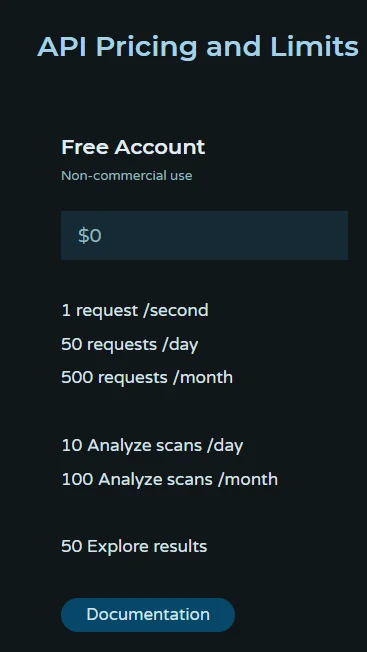
API Pricing for Pulsedive
Pulsedive’s user interface is constructed using the API, which means users have been interacting with it all along. As they suggest, this design ensures that most functionalities available in the UI are also accessible through the API, offering great flexibility. There is a free version that does not impose extreme restrictions for non-commercial use.
4. AbuseIPDB
AbuseIPDB sets itself apart from other platforms on our list by providing a singular IoC format. However, this specialized focus distinguishes it in this aspect.
AbuseIPDB is a project committed to combating the proliferation of hackers, spammers, and abusive behavior on the internet. Their goal is to contribute to a safer online environment by offering a centralized blacklist. This platform serves webmasters, system administrators, and individuals interested in reporting or identifying IP addresses linked to malicious activities online.
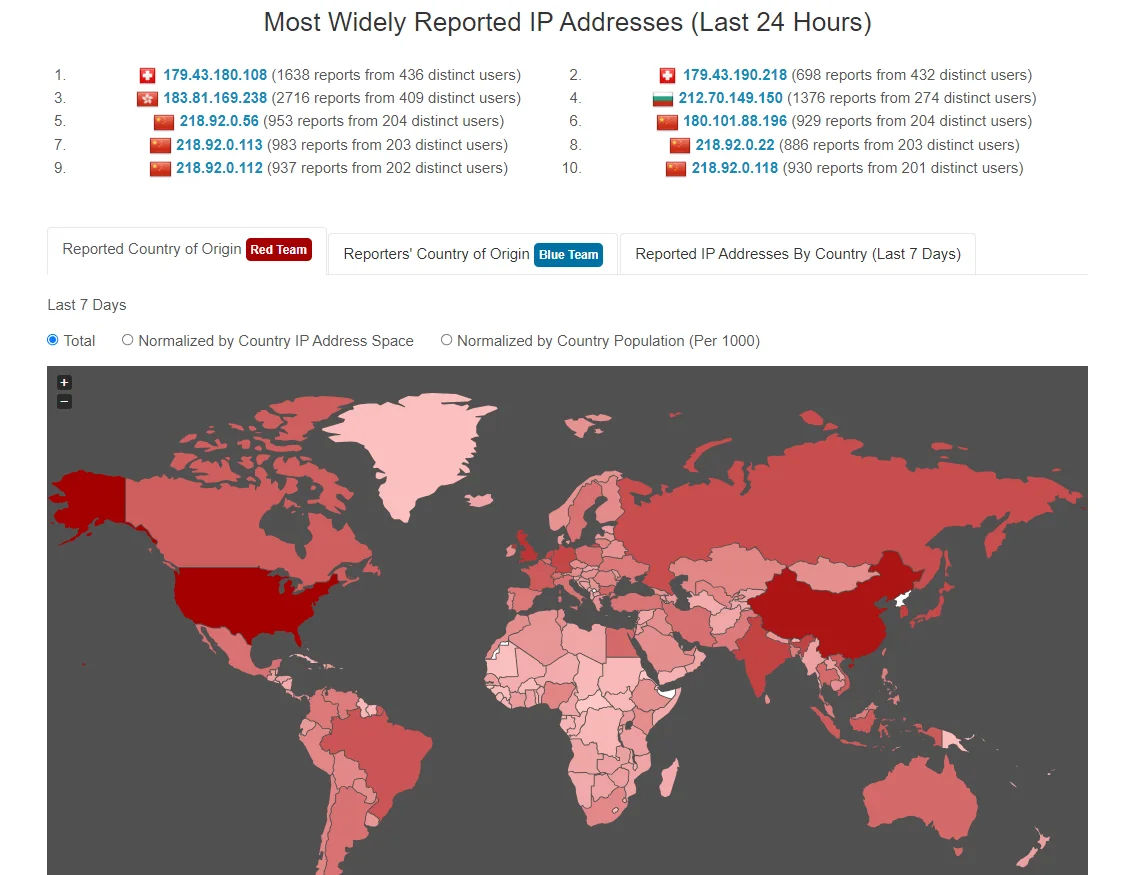
AbuseIPDB has a statistics section, one intriguing aspect of this section is its ability to generate a table showcasing the locations targeted by attacks, which is curated organically through reports from the community.
Users can either report an IP address associated with malicious activities or verify if an IP address has been reported using the search box provided above. Of course, it is possible to perform IP checks via the website, but AbuseIPDB also has many integration channels, therefore could lighten up the work of SOC analysts.
Integration with many popular tools and platforms for blue teams
There is a free API plan for individual use that supports up to 1.000 IP checks per day.
5. RST Cloud
RST Cloud is a provider of scalable and flexible threat intelligence and data enrichment solutions that help users with their cybersecurity efforts. The platform distinguishes itself through its comprehensive approach to collecting, analyzing, and contextualizing threat data, which is critical for understanding and mitigating cyber threats.
RST Cloud’s key features include a comprehensive threat intelligence engine that aggregates data from multiple sources, including sandboxes and its own honeypot network, to provide contextualized threat intelligence.
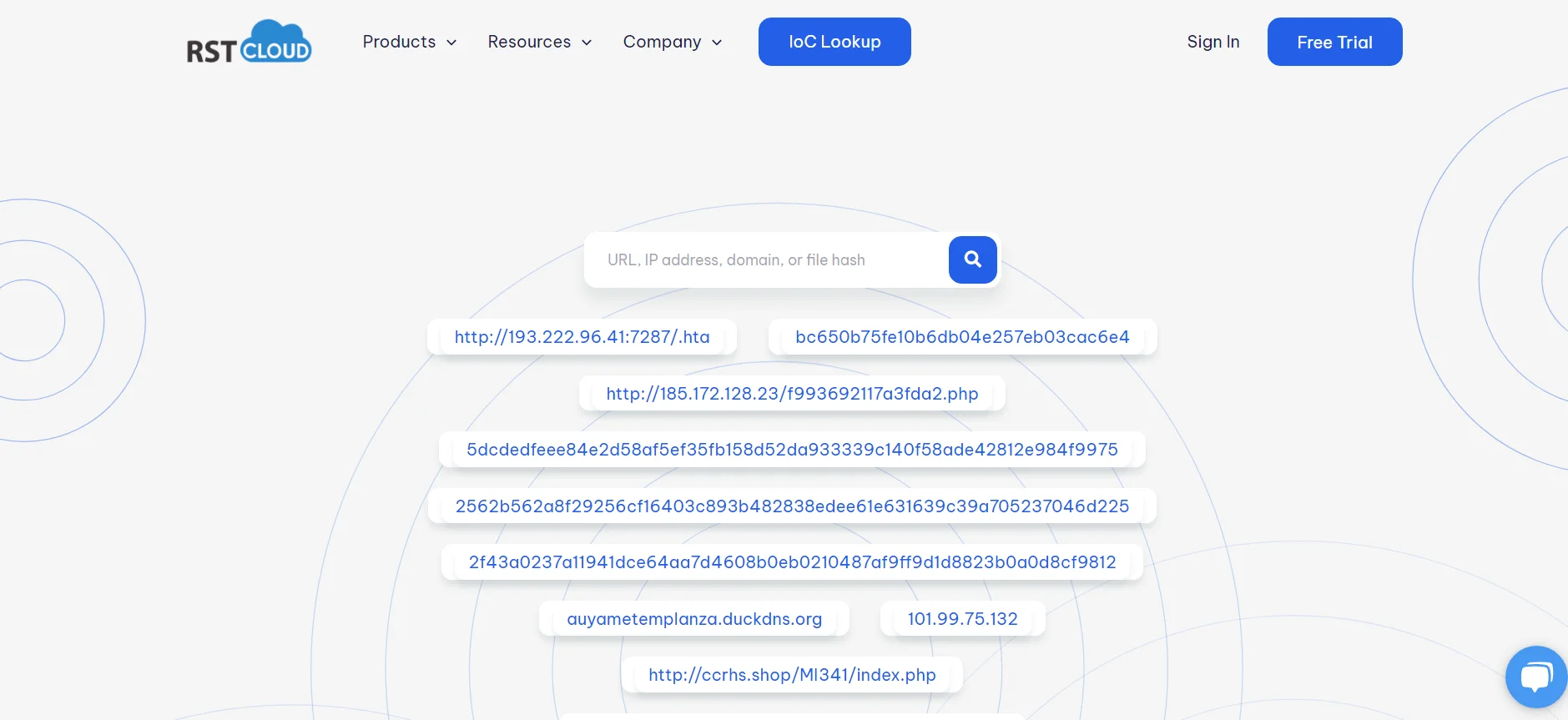
RST Cloud IoC Lookup
The platform provides detailed information about threat categories, malware families, threat actors, and vulnerabilities, which is critical for accurate threat detection and response. RST Cloud integrates seamlessly with popular security tools such as SIEM, SOAR, NGFW, and TIP, thereby improving existing security workflows.
The platform collects IoCs from various open and community-supported sources, enriching and ranking them to help cybersecurity professionals consolidate their knowledge of publicly available threat intelligence sources. A script is available that downloads IoCs from RST Cloud and imports them into MISP (Malware Information Sharing Platform & Threat Sharing) for analysis, which is useful for organizations that use MISP for threat intelligence.
However, apart from a free trial, there is no free version.
6. GreyNoise
As stated on their website, GreyNoise is dedicated to gathering, evaluating, and categorizing data concerning Internet Protocol (IP) addresses that engage in scanning activities across the web, inundating security systems with superfluous data. This unique vantage point aids analysts by minimizing the time spent on irrelevant or innocuous actions, allowing them to focus more on pinpointing and addressing specific and emerging threats.
The platform enhances Security Operations Center (SOC) efficacy by mitigating the impact of noisy alerts, deprioritizing events originating from benign IPs and common business services. It expedites the classification of IP intent, thereby reducing the time required for triage. Furthermore, GreyNoise automates workflows and streamlines the filtration of noisy alerts across various security tools such as Security Information and Event Management (SIEM), Security Orchestration, Automation and Response (SOAR), Threat Intelligence Platform (TIP), and others.
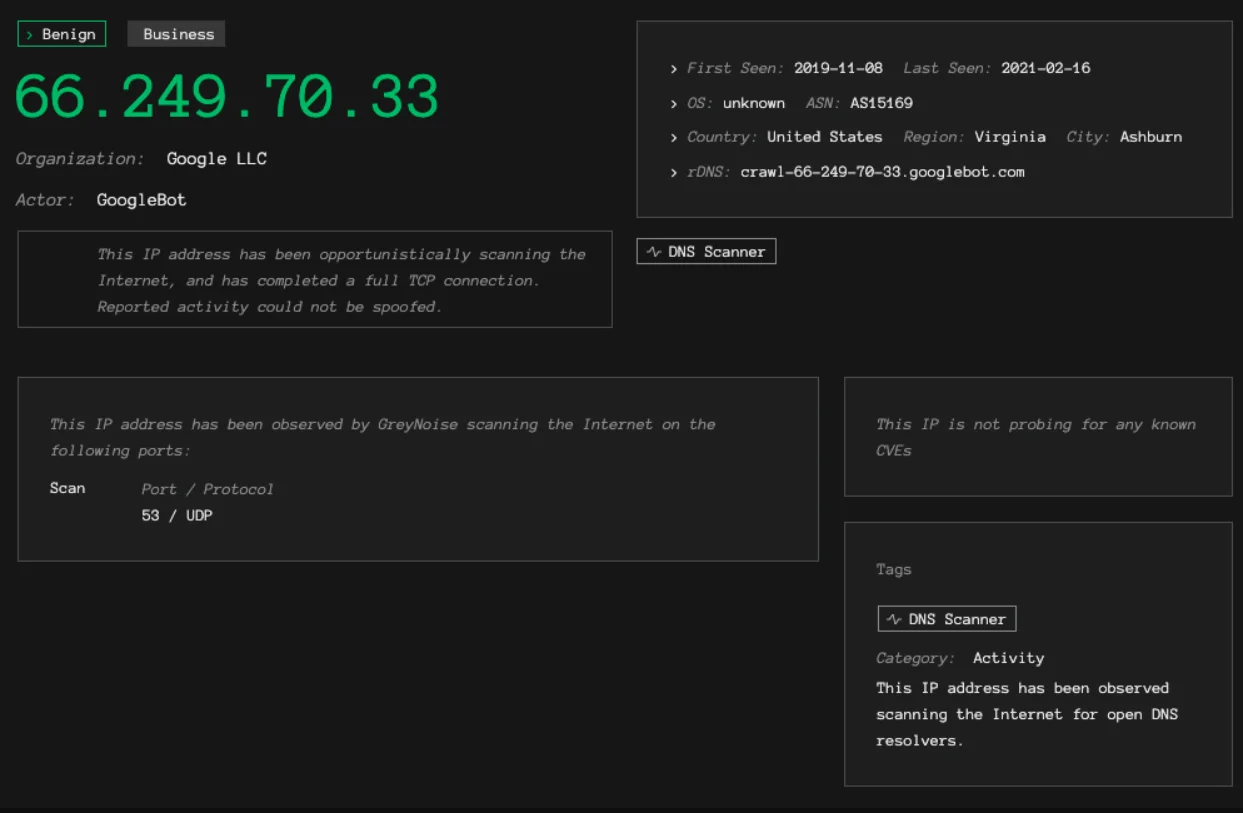
GreyNoise, focused on aiding SOC team
The system aids in defending against mass exploitation by providing visibility into activities related to mass exploits targeting your attack surface. It facilitates the creation of IP blocklists during periods of exposure, prioritizing patching efforts. Additionally, by blocking IPs associated with mass exploit attacks at the network perimeter, GreyNoise affords organizations the breathing room needed to implement necessary patches effectively.
Moreover, GreyNoise enables contextualization and automation of threat hunting endeavors. It empowers threat hunters to uncover the Tactics, Techniques, and Procedures (TTPs) utilized by adversaries through comprehensive attack telemetry. The platform also bolsters and automates ongoing cyber threat investigations by leveraging IP metadata, enhancing the overall efficacy of cybersecurity operations.
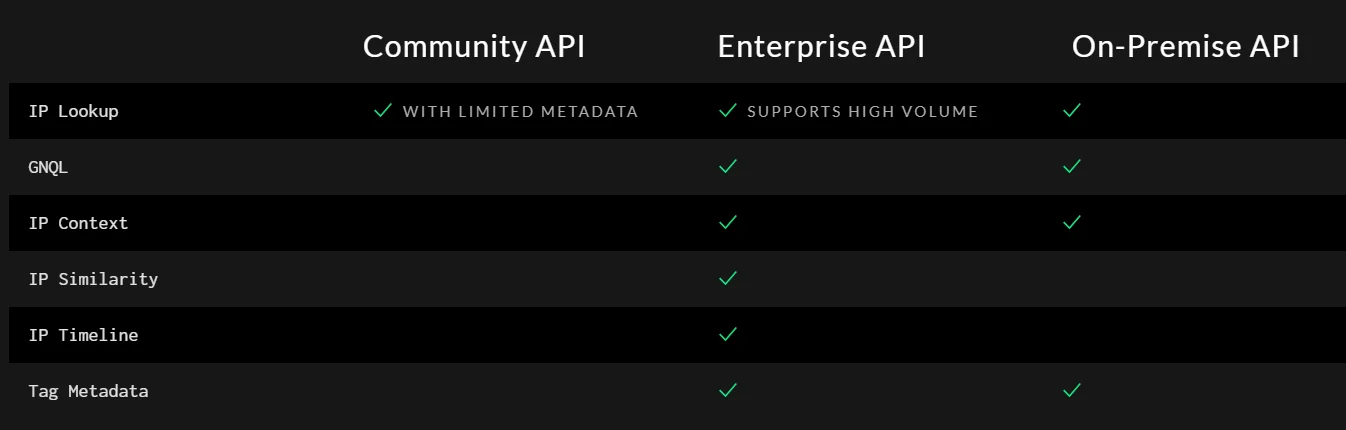
Community API only has IP Lookup feature
Just like other platforms, GreyNoise offers API integration free of charge for personal use, albeit with extended limitations. GreyNoise furnishes a wide range of APIs tailored for both our community and commercial clients, along with a supported Python SDK designed to facilitate development processes.
7. MISP Threat Sharing
MISP, an open-source threat sharing platform, offers a comprehensive suite of features tailored for managing Indicators of Compromise (IoCs) and enriching threat intelligence across diverse domains such as targeted attacks, financial fraud, vulnerabilities, and counter-terrorism. We should also add that MISP also contributes to many of the platforms we write about here.
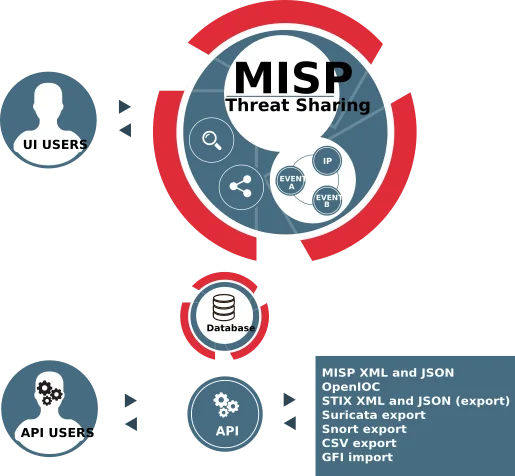
MISP Threat Sharing
MISP’s key strengths lie in its ability to facilitate the sharing, storage, and correlation of IoCs related to cybersecurity, malware analysis, and beyond. It serves as an efficient IoC and indicators database, accommodating both technical and non-technical information about malware samples, incidents, attackers, and intelligence.
The platform’s automatic correlation engine is particularly noteworthy, capable of identifying relationships between attributes and indicators from various sources, including malware, attack campaigns, and analysis reports. Advanced correlation methods such as Fuzzy hashing (e.g., ssdeep) and CIDR block matching enhance the platform’s analytical capabilities.
MISP’s flexible data model enables the expression and linkage of complex objects, empowering users to articulate threat intelligence, incidents, and connected elements effectively. This versatility extends to its built-in sharing functionality, which supports multiple distribution models and synchronization capabilities across different MISP instances. The platform also offers advanced filtering options to align with organizational sharing policies, including granular sharing group controls and attribute-level distribution mechanisms.
From a user perspective, MISP provides an intuitive interface for creating, updating, and collaborating on events, attributes, and indicators. The graphical navigation and event graph functionality facilitate seamless exploration of relationships between objects and attributes, enhancing analysts’ ability to contribute effectively.
Moreover, MISP’s export capabilities cover a wide range of formats, including IDS rules (Suricata, Snort, Bro), OpenIOC, plain text, CSV, and JSON, enabling seamless integration with other security systems. Import functionalities, including bulk and free-text imports, further enhance interoperability with external data sources such as GFI sandbox, ThreatConnect, and MISP feeds.
The platform’s collaborative nature extends to its support for data-sharing with other parties and trust-groups, streamlined feed imports, and delegated sharing mechanisms. Integration with PyMISP, a flexible Python library, allows for custom solutions and expands MISP’s functionality.
MISP source code is available on GitHub including documentation and scripts for installation.
8. VirusTotal
VirusTotal serves as an online platform where users can assess files and URLs for potential Malware threats. It functions as a centralized hub, fostering a collaborative cybersecurity approach through the utilization of numerous antivirus engines and additional security tools. By aggregating and scrutinizing data from diverse origins and from its partners including SOCRadar, VirusTotal offers in-depth insights into the security posture of files and URLs.
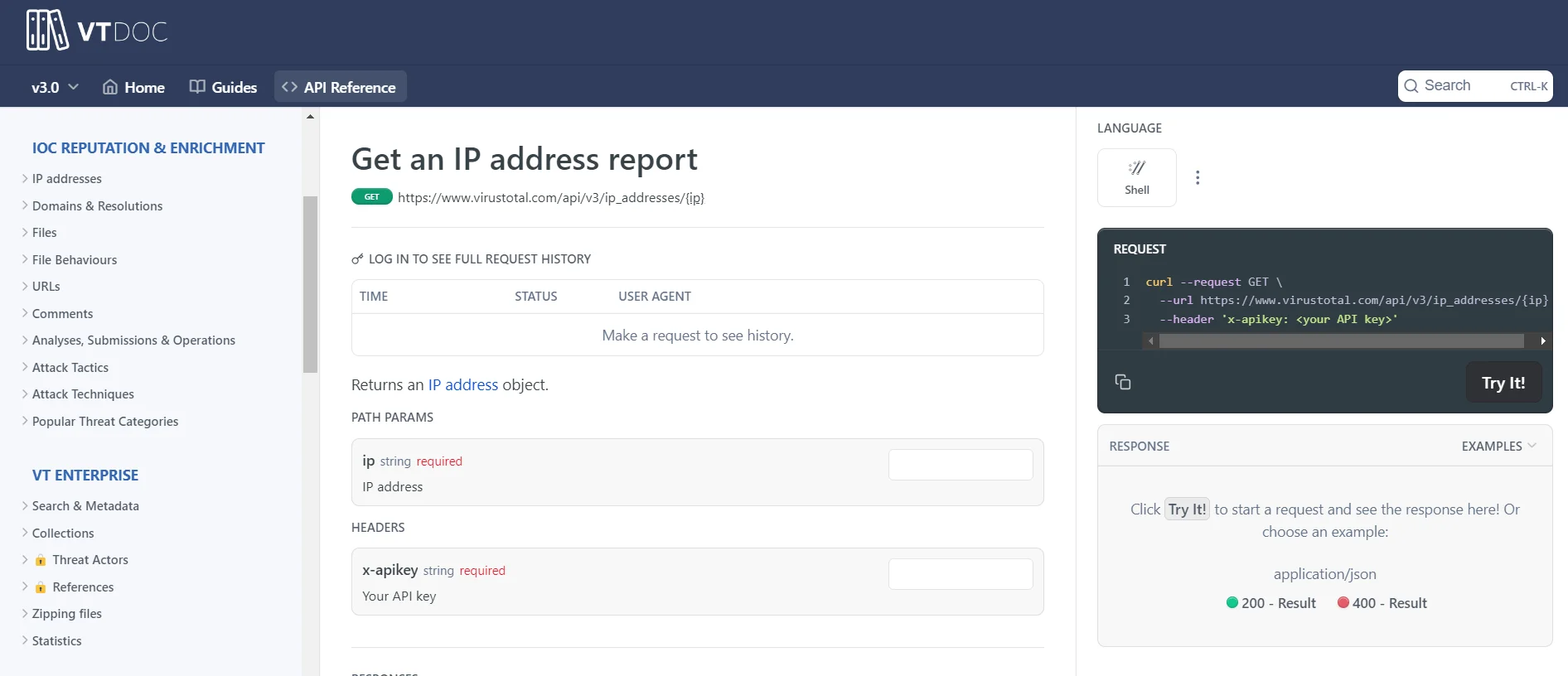
VirusTotal has a very detailed documentation for its API
IoC enrichment is not the first thing that comes to mind when VirusTotal is mentioned for many. However it turns into a very versatile tool especially with the VirusTotal API.
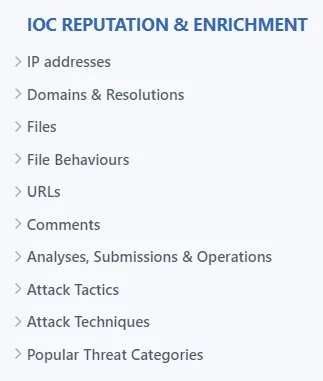
VirusTotal documents about IoC Reputation & Enrichment
Furthermore, VirusTotal seamlessly integrates with nearly all SIEM platforms. In this scenario, when a security alert surfaces, VirusTotal enhances it by furnishing crucial threat data such as detections, attributes, associations, behaviors, and more. This enrichment aids security operators in effectively prioritizing these alerts.
The VirusTotal API facilitates file or URL uploads and scans, grants access to completed scan reports, and enables automated comments without reliance on the website interface. Essentially, it empowers the creation of straightforward scripts for accessing all of VirusTotal’s generated information.
9. ThreatBook
ThreatBook Intelligence offers cybersecurity solutions, prioritizing accuracy, efficiency, and actionable responses for organizations.
ThreatBook Intelligence’s main page
As they claim, their intelligence, sourced from real customer cases, ensures high accuracy, aiding SOC teams in making informed decisions swiftly. This data-driven approach allows clear verdicts, behavioral conclusions, and detailed intruder profiles, streamlining operations and reducing non-critical task loads.
With a focus on accurately identifying compromised hosts and emerging threats like mining pools and ransomware, they enable rapid response strategies and effective risk mitigation. Their API seamlessly integrates with existing systems, providing comprehensive insights into domains, malicious samples, and real-time threat analysis.
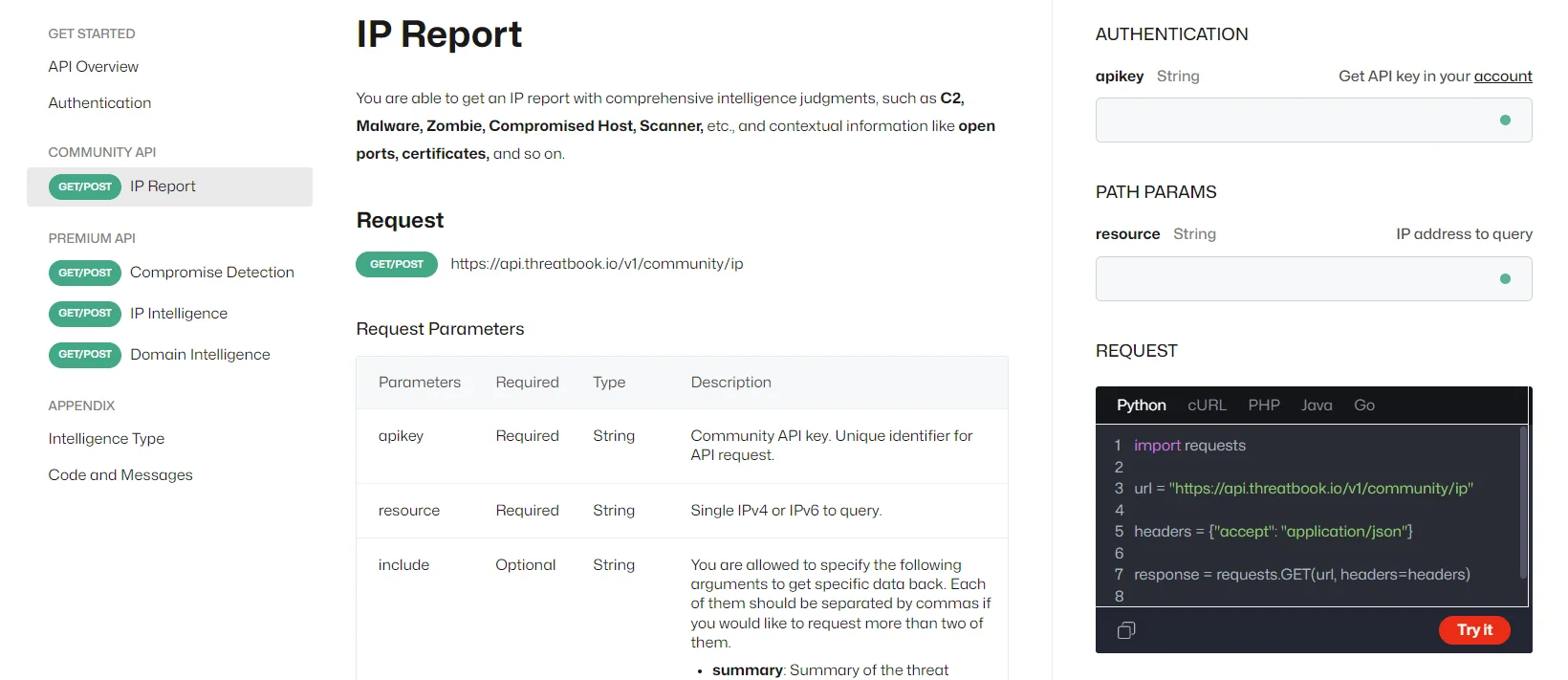
ThreatBook’s Community API only has IP Report function
Their community API only works for IP reports but has different parameters. IP reports encompass comprehensive intelligence assessments, including C2, Malware, Zombie, Compromised Host, Scanner, and more, along with contextual details such as open ports, certificates, and additional relevant information.
10. SOCRadar’s Threat Feed / IOC
SOCRadar has many modules, and platform users benefit from them as a package. However, it also contains features that can be used for a single purpose.
SOCRadar’s Threat Feed & IOC module is a comprehensive cybersecurity solution that delivers enriched data and actionable intelligence to help organizations stay ahead of cyber threats. This module is intended to provide cybersecurity teams with comprehensive and enriched data, serving as a critical resource for researching and combating cyber threats.
The module includes user-friendly dashboards that enable professionals to customize feeds based on their specific requirements. It allows users to stay up to date on recent threats, easily search for Indicators of Compromise (IoCs), and benefit from seamless integration with their systems via the TAXII protocol.
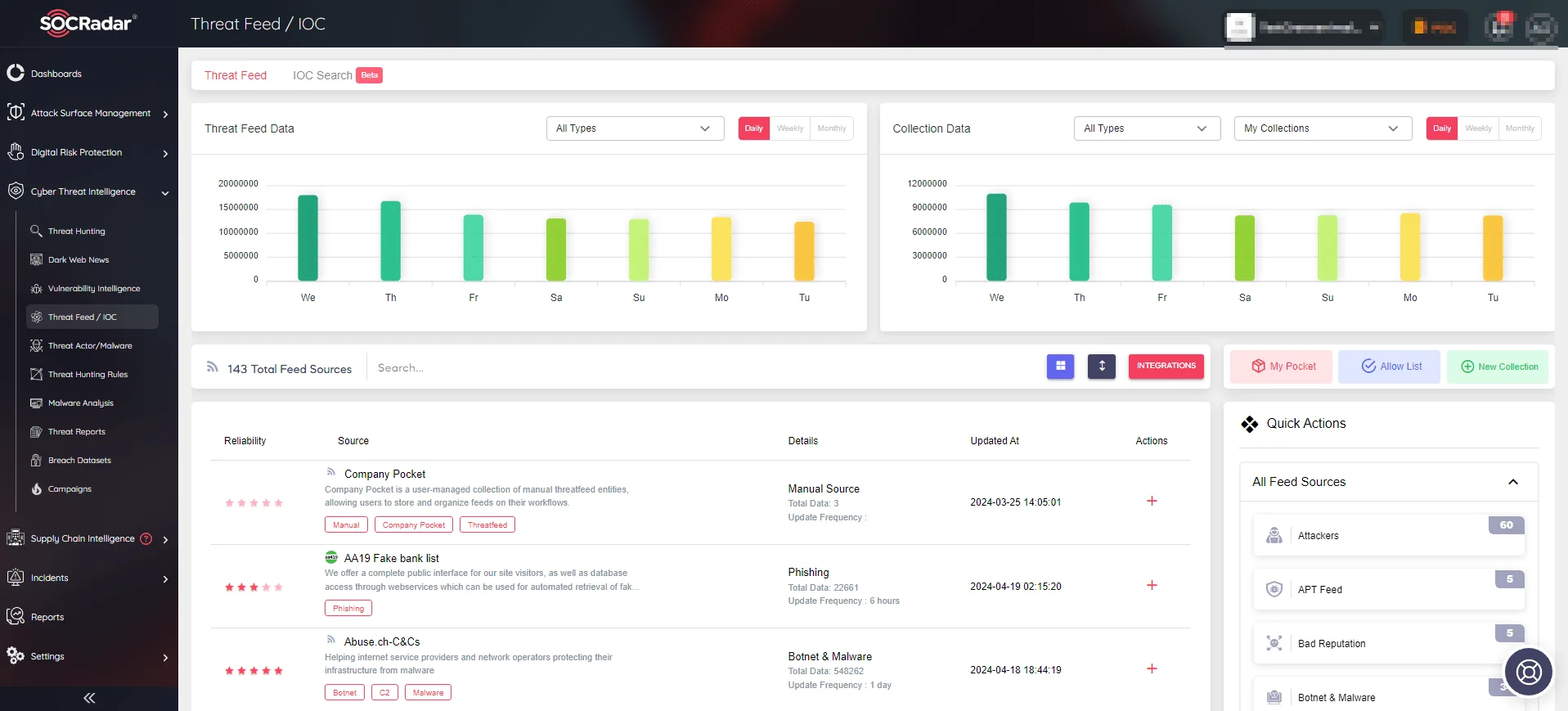
SOCRadar’s Threat Feed & IoC Management module
Furthermore, the module supports bulk searches, which enable users to query multiple IoCs or IPs from a single screen. This functionality is extremely useful, especially when defenders are dealing with newly emerging threats and time is critical.
SOCRadar combines a variety of threat feeds, transforming massive amounts of data into actionable intelligence. This enables rapid detection, thorough analysis, and effective response to emerging threats, thereby strengthening an organization’s resilience in the ever-changing cyber landscape.
Test the module’s IoC search capabilities using SOCRadar Labs’ IoC Radar, which is a supplementary and a free version.

SOCRadar Labs’ IoC Radar