
Dark Web Monitoring with Open-Source Tools and Services
The dark web, intentionally hidden on the internet, is accessible only through specialized browsers or technologies. Defenders monitor it for clues on potential cyber threats, leveraging various tools, from CTI platforms to community-driven open-source services.
But, why is the dark web so significant for cybersecurity? Some threat information that analysts can find on the Dark Web includes:
- Data in leak or sale posts, such as names, email addresses, passwords, financial and corporate information, and more.
- Exploits for security vulnerabilities, even zero-days.
- Administrator access sales to certain technologies and systems.
- Sale of tools that could facilitate hacking campaigns, such as phishing kits, stealers, and ransomware services (check specifics about RaaS).
- Cyber attack campaigns that have been announced by attackers, or are still in the planning phase.
Monitoring the dark web yields insights into future threats, making it vital for the security posture of businesses. Across all industries, especially in government, finance, and technology, defenders require intelligence on specific cyber threats on their radar, and tracking the dark web offers them additional context. This is why SOCRadar diligently tracks numerous hacking forums, black markets, and hacker channels across the dark maze – to provide organizations with essential intelligence to protect their digital assets.
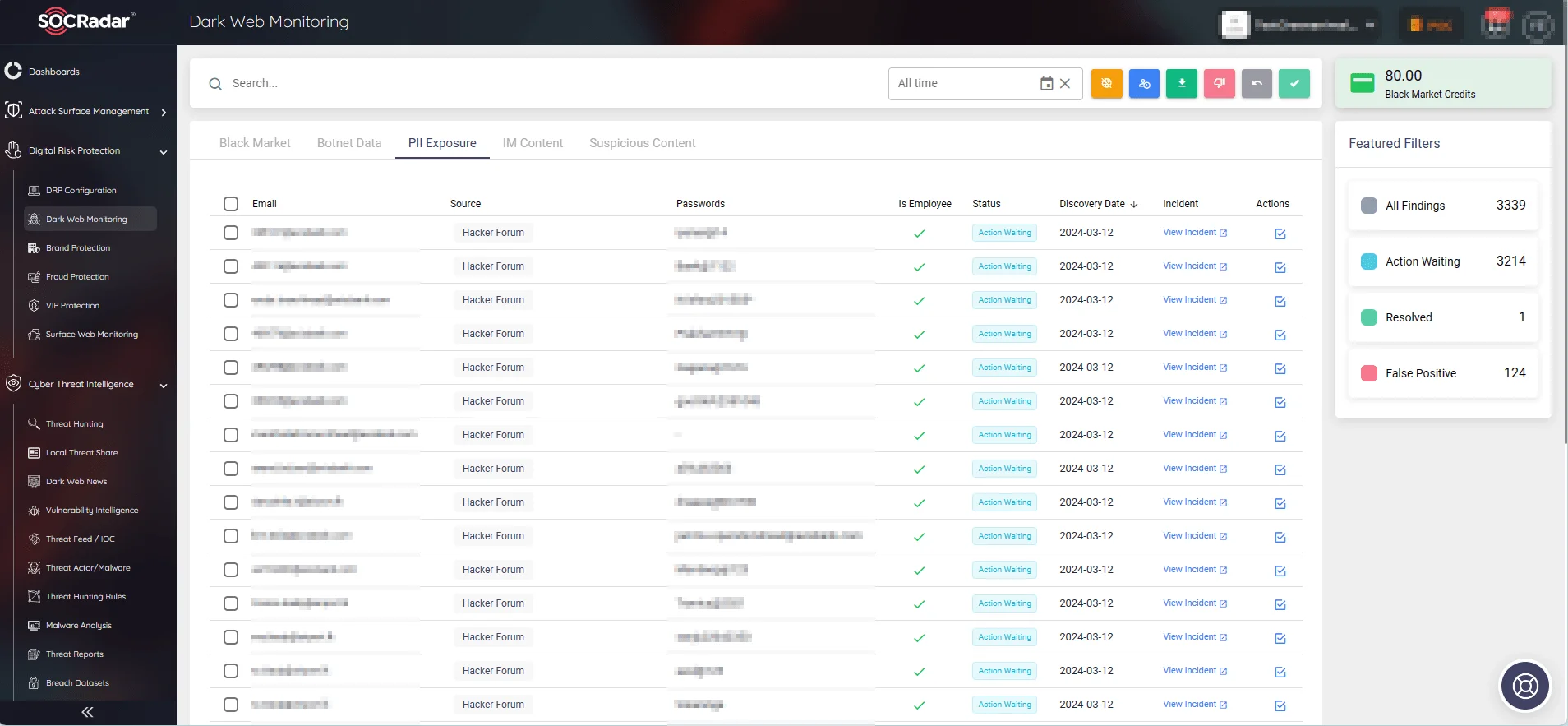
SOCRadar’s Dark Web Monitoring
Using open-source tools in pursuit of dark web monitoring has several advantages, including accessibility, customization, cost-effectiveness, and flexibility. These tools enable organizations to gain insights with peace of mind, as they can inspect the code of these tools and services and integrate them accordingly with their infrastructure and security needs.
In this blog post, we will explore some of the top open-source tools for dark web monitoring, that may help you scan, inspect, and identify threats effectively.
OWASP TorBot
OWASP TorBot is a Python-based open-source tool designed for crawling hidden websites with “.onion” addresses. The project is open to contributions and its code is fully available on GitHub.
TorBot – Open Source Intelligence Tool for the Dark Web
Its features include retrieving page titles and addresses along with short descriptions, saving crawl information to JSON files, crawling custom domains, and checking the live status of links.
With its comprehensive functionality, TorBot streamlines the process of information collection on the Dark web using OSINT techniques. Its user-friendly interface and valuable output make it a great tool for efficiently gathering essential data from dark web pages, thereby simplifying and expediting the information collection process.
MISP (Malware Information Sharing Platform)
Malware Information Sharing Platform, shortly MISP, stands as a widely-known open-source tool centered on shared threat intelligence data.

MISP – Malware Information Sharing Platform
MISP offers versatile software that can be deployed in data centers or on diverse cloud platforms, utilizing open-source protocols and data formats for seamless integration with other information security tools.
Despite its threat streams lacking the curation found in commercial solutions, MISP provides a cost-effective means for organizations to establish an internal dark web monitoring system. Its interoperability and support for integration with various security solutions make it a valuable asset for enhancing threat intelligence capabilities and bolstering cybersecurity defenses.
Organizations can integrate services with MISP to exchange threat intelligence data, including information about dark web activities. This integration allows them to customize their monitoring by choosing risk levels, data transfer frequencies, and specific event tags tailored to their needs.
OnionScan
OnionScan is yet another tool for Dark Web exploration, offering a free and open-source solution for safely traversing the hacker grounds.

Explore more about OnionScan on GitHub
Despite the remarkable advancements in anonymity and privacy technologies, the perennial threat of human error persists unabated. Designed for security experts, OnionScan helps uncover vulnerabilities and misconfigurations in hidden services, promoting the secure utilization of the dark web.
Its goals are twofold: assisting service operators in improving security and aiding researchers in monitoring Dark Web sites.
OnionScan works by scanning .onion addresses for sensitive information that could compromise anonymity. For example, it examines metadata in uploaded images, exposed server status pages that may reveal true IP addresses, and shared encryption keys that may indicate connections between sites.
Eventually, it can generate a variety of reports, ranging from simple summaries categorizing risk levels to detailed outputs in verbose or JSON formats that can be easily integrated with other tools.
Ahmia.fi
Ahmia.fi, born out of the Tor Project by Juha Nurmi, addresses the unique challenge of navigating the TOR Network’s architecture.
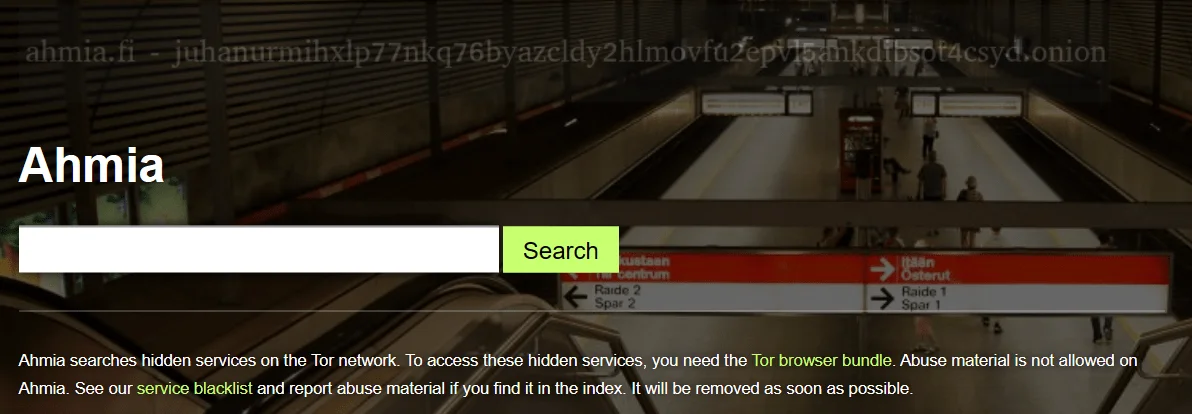
Ahmia.fi search page
Unlike traditional search engines, Ahmia specializes in indexing .onion URLs from the Tor network, creating one of the most comprehensive deep web indexes available.
By aggregating these URLs, Ahmia provides users with access to otherwise hidden content. Notably, Ahmia’s open-source nature allows users to access its source code on GitHub, enabling them to build their own index and crawler for personalized deep web exploration.
We previously included Ahmia in our article “Top 5 Dark Web Search Engines,” highlighting its utility. For a deeper context on various dark web tools and services, check out the article.
Key Features to Look for in Dark Web Monitoring Solutions & SOCRadar’s Advanced Toolkit
A typical dark web monitoring tool actively scours the dark web for any mentions of your company’s information or data. Scanning hundreds of sites, it provides valuable insights into dark web activity and triggers alerts for threats that may affect your organization.
Advanced tools go further by generating reports on the data found, translating it into actionable insights.
Key features of an effective dark web monitoring solution include access to a wide range of dark web platforms, threat hunting capabilities, continuous monitoring, and real-time alerts. Integration with existing security infrastructure is also critical for enhanced response capabilities.
Fitting the profile, SOCRadar’s Dark Web Monitoring service is a vital component of our cybersecurity suite, offering real-time capabilities to track potential risks within the dark web ecosystem. It detects exposures of employee, customer, and corporate information, unauthorized data transfers, and identifies threat actors and malicious activities associated with your company, providing timely alerts.
While our platform is not open-source, it offers advanced measures for delivering purposeful dark web intelligence and seamless integrations. With Dark Web News, users can monitor the latest discussions on deep and dark web forums, including hacker channels on Telegram.
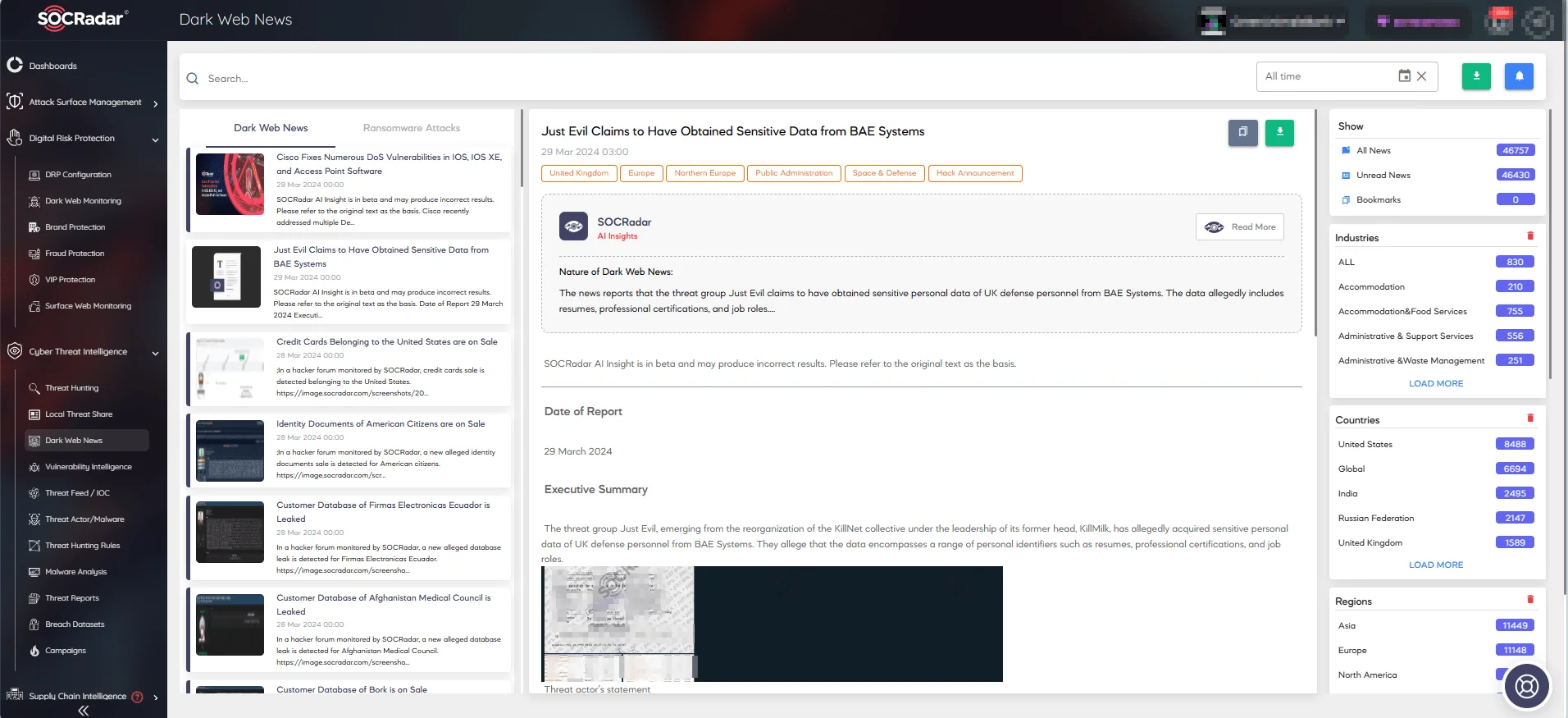
SOCRadar’s Dark Web News
Additionally, our XTI platform features Threat Hunting capabilities, enabling users to filter through vast amounts of data and analyze stealer logs to monitor exposures.
Tailored to address industry-specific cybersecurity challenges, SOCRadar ensures organizations are equipped to counter sector-specific threats. Our comprehensive approach includes curated reports for timely industry or country-based intelligence on Dark Web threats.
Conclusion
Through the use of various tools and services, including open-source solutions like OWASP TorBot, MISP, OnionScan, and Ahmia, defenders can navigate the complexities of the dark web to extract valuable intelligence.
The dark web is extremely important in the field of cybersecurity, providing analysts with a wealth of valuable threat intelligence. Its depths contain a treasure trove of sensitive data, including leaked information, security vulnerabilities, administrator access offerings, illegal hacking utility sales, and the disclosure of impending cyber attack strategies.
In addition to these invaluable open-source tools, SOCRadar presents a comprehensive approach with its suite of Dark Web Monitoring tools. While open-source tools provide accessibility and cost-effectiveness, SOCRadar’s advanced toolkit offers enhanced functionality and seamless integrations. With its Dark Web Monitoring service, SOCRadar provides real-time capabilities for tracking potential risks within the dark web ecosystem, issuing timely alerts and actionable insights.
By combining the capabilities of these tools and services, businesses can boost their defenses against the unpredictable threats lingering in the dark web. Whether scanning, assessing, or identifying threats, the tools discussed in this article, as well as SOCRadar’s advanced toolkit, provide valuable resources for improving cybersecurity measures and remaining far ahead of potential threats.




































