
Attack Surface Management with Open-Source Tools and Services
As the first line of defense against cyber attacks, adept attack surface management is critical in reducing the chance of a successful breach, protecting firms from the possible consequences of severe financial and reputational harm proactively.
The increase in the number of Internet of Things (IoT) devices, the widespread shift to remote work, and the growing adoption of cloud services in an era of increasing digitalization all play important roles in the ongoing expansion of the attack surface.
As the digital landscape expands, so does the canvas for security challenges. Potential attackers seek out fertile ground and capitalize on each new addition of devices or technologies to conduct malicious activities. Adding to the complexity, the dynamic nature of cyber threats necessitates that organizations remain vigilant, constantly updating their security practices to stay ahead of emerging attack vectors.
In this blog post, we will examine popular open-source tools and services that can help you navigate this complex landscape, and effectively enhance attack surface management practices.
Advantages of Using Open-Source Tools/Services in Attack Surface Management
Understanding and managing your attack surface is a cornerstone of effective defense. The attack surface represents the cumulative vulnerabilities and potential entry points that could be exploited by malicious actors. Robust attack surface management is essential, acting as a proactive defense mechanism against cyber threats.
Attack Surface Management involves the systematic identification, classification, monitoring, and reduction of an organization’s attack surface. By comprehensively mapping potential vulnerabilities, businesses can fortify their defenses and minimize the risk of exploitation. It is a continuous process, adapting to the ever-evolving digital landscape.
In this pursuit, the choice of tools is critical. Open-source tools offer a compelling advantage in terms of accessibility, customization, and community support. These tools empower organizations to gain granular insights into their attack surface without the constraints of proprietary solutions.
Here is why open-source tools prove to be advantageous:
- Cost-Effective Solutions: Open-source tools are often free or less expensive than proprietary alternatives, making them available to a wider range of organizations.
- Community Collaboration: The open-source community thrives on collaboration and sharing knowledge. Leveraging these tools entails engaging in a collective intelligence pool, where problems are identified and solutions are developed collaboratively.
- Customization and Flexibility: Open-source tools allow you to tailor solutions to specific organizational needs. This adaptability is critical in the dynamic environment of attack surface management.
- Transparency and Trust: The transparency inherent in open-source projects fosters trust. Organizations may inspect the code to ensure that the tools meet their security and compliance standards.
Top Open-Source Tools/Services for Navigating Your Attack Surface
There is a variety of open-source tools designed to enhance the monitoring of organizations’ attack surfaces, offering accessible solutions for entities of all sizes to strengthen their cybersecurity defenses.
Below are well-known examples of such tools, including Nmap and OpenVAS, which provide network and vulnerability identification and inventory capabilities, and others.
Nmap (Network Mapper)
Nmap, an abbreviation for Network Mapper, is perhaps the most well-known of the extensive arsenal of open-source utilities, providing powerful capabilities for network discovery and security auditing.
It is widely used by network administrators and security professionals, and its versatility makes it a preferred tool for network mapping and analysis. Nmap excels at identifying hosts and uptime, running port scans, and more, providing a thorough means to monitor and inventory network devices while meticulously mapping out your attack surface.
Nmap’s ability to detect operating systems improves a defender’s understanding of network infrastructure and identifies potential vulnerabilities unique to each system. It also detects version numbers and provides information about the software and services that run on the network.
Nmap performs port scans, revealing open ports and services, allowing administrators to assess potential entry points for threat actors.
The tool’s functionality is further expanded by the Nmap Scripting Engine (NSE), which allows users to write and execute custom scripts that automate a variety of networking tasks, such as vulnerability scanning and network exploration.
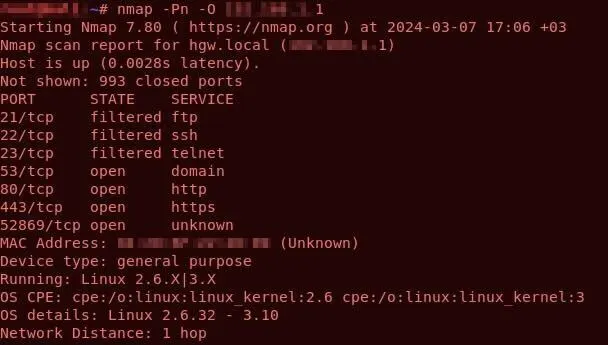
Scanning with Nmap
OpenVAS (Open Vulnerability Assessment Scanner)
OpenVAS is useful for managing attack surfaces with its usage in reducing security risks by identifying potential attack vectors and vulnerabilities. It performs vulnerability scans that include port scanning, service detection, and testing for known flaws and misconfigurations.
OpenVAS maintains a large database to ensure a thorough evaluation of potential threats. Its commitment to regular updates ensures that the framework can detect new vulnerabilities and provide up-to-date protection.
The OpenVAS tool is scalable, allowing users to run it on a single server or in a distributed architecture.
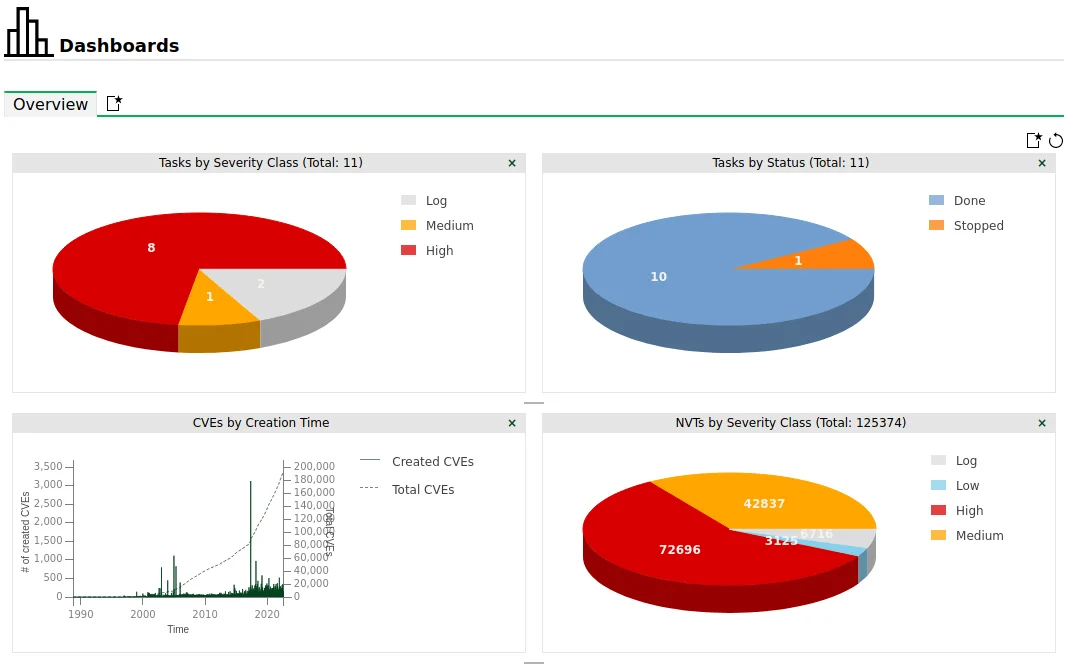
OpenVAS dashboards
Findomain
Findomain, an open-source tool utilized for subdomain enumeration and discovery, offers both free and priced plans, with the latter providing enhanced capabilities. Leveraging Certificate Transparency logs and various APIs, Findomain swiftly identifies subdomains linked to a specified domain across multiple platforms including Linux, Windows, macOS, and Android.
In the field of Attack Surface Management, Findomain proves useful in several aspects:
- Subdomain Discovery: Findomain assists security professionals and organizations in identifying subdomains associated with their target domain. Discovering these subdomains allows them to gain a better understanding of their attack surface and potential vulnerabilities.
- Asset Inventory: Findomain helps to generate an asset inventory and continuously scan internet-facing assets for vulnerabilities, providing visibility into organizations’ external ecosystem.
- Automation and Integration: Findomain offers features like multi-thread support, integration with other tools, and the ability to send data to webhooks for automation and centralized findings.

Findomain, domain recognition tool
Dismap
Dismap, developed in the Golang language, is an open-source asset discovery and identification tool renowned for its swift recognition of web fingerprint information and diverse asset types associated with a target domain.
With a robust library of fingerprint rules including TCP/UDP/TLS protocol fingerprints and 4500+ web fingerprint rules, users can tailor recognition rules to their requirements, while its capability to scan IP addresses and target URLs offers flexibility in assessing the attack surface.
In the context of Attack Surface Management, Dismap excels in asset discovery by swiftly identifying assets linked to a target domain, aiding in mapping the attack surface and highlighting potential vulnerabilities. Its rapid detection of web fingerprint information facilitates vulnerability assessment, enabling security teams to prioritize and mitigate vulnerabilities effectively.
Moreover, Dismap supports automation and integration with other tools, streamlining the attack surface management process and enhancing overall efficiency.
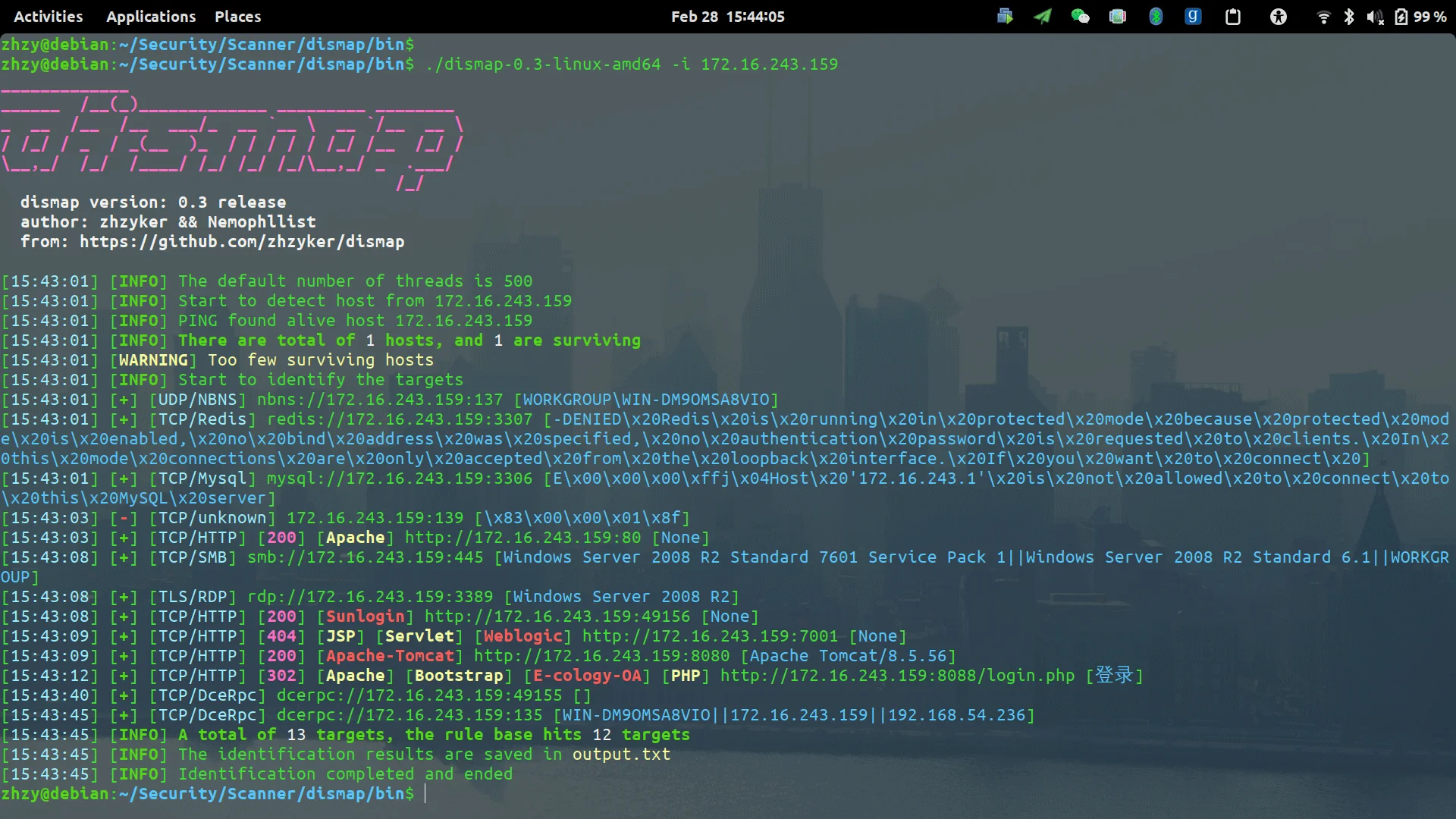
Asset discovery with Dismap
SonarSearch
SonarSearch offers a rapid API for accessing Rapid7’s Project Sonar dataset, which contains valuable internet-wide scan data, including subdomains and related information.
Although the Project Sonar dataset was once publicly available, Rapid7 has restricted access to it, rendering the data hosted on the omnisint API outdated. However, a guide on GitHub exists for setting up a self-hosted instance of the API, provided users can acquire a dataset:
SonarSearch v2 on GitHub
In the realm of Attack Surface Management, SonarSearch proves valuable in subdomain enumeration and asset discovery. Using SonarSearch, security professionals can discover subdomains associated with target domains and glean insights into open ports, SSL certificates, and more, thereby enhancing their understanding of potential vulnerabilities within the attack surface.
Despite its offline status, SonarSearch remains a potent resource for gathering threat intelligence and discerning trends, patterns, and risks associated with specific domains or IP addresses.
reNgine
reNgine is a pioneering open-source automated reconnaissance framework tailored for web application penetration testing, aiming to streamline the reconnaissance process by offering a highly configurable suite of tools.
One of reNgine’s standout features is its highly configurable reconnaissance process, empowering users to customize their approach using various engines. This streamlined method simplifies the gathering of reconnaissance data with minimal configuration, benefiting penetration testers and security auditors alike.
Additionally, reNgine supports continuous monitoring, enabling users to schedule scans at regular intervals. Notifications via platforms like Discord, Slack, or Telegram keep users informed about new subdomains, vulnerabilities, or changes in reconnaissance data.
In version 2.0, reNgine introduced integration with GPT, facilitating the identification of potential attacks on subdomains. Leveraging reconnaissance data such as page titles, open ports, and subdomain names, reNgine offers insights into likely successful attack strategies.
It is important to note that reNgine is not a vulnerability scanner; rather, it focuses on automating the reconnaissance phase of web application penetration testing. It centralizes gathered information, presents clear results, and allows for flexible customization of the reconnaissance pipeline.
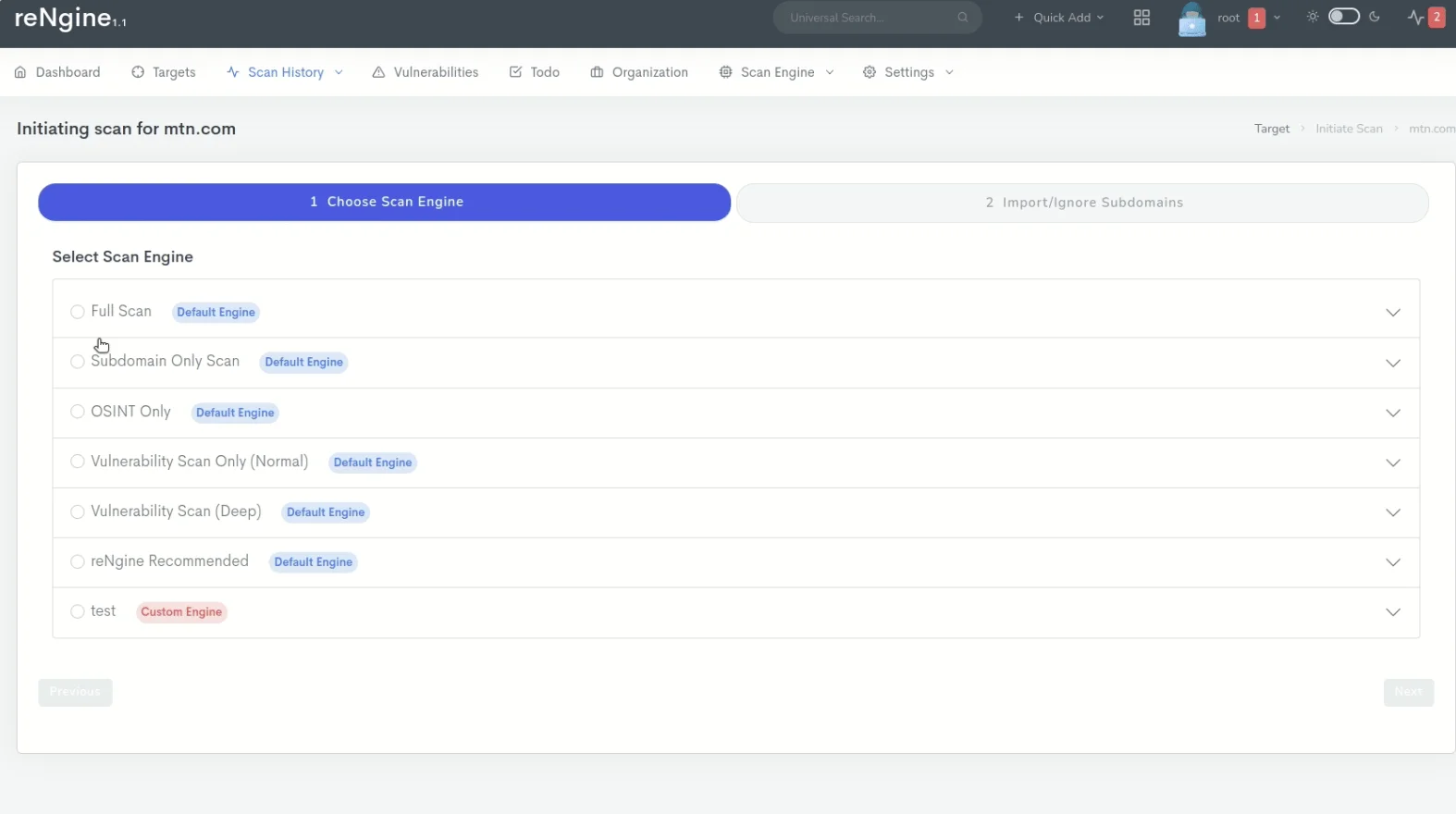
Initiating scans on rEngine
OWASP Amass Project
The OWASP Amass Project is an open-source framework created by the Open Web Application Security Project (OWASP) to help information security professionals map network attack surfaces and discover external assets using open-source intelligence gathering and reconnaissance methods.
The framework includes several components:
- Collection Engine: The collection engine is responsible for in-depth attack surface mapping and asset discovery. It utilizes various techniques and tools to gather information about the target network and assets.
- Amass Tool: The Amass tool is a command-line interface (CLI) tool that allows users to execute the collection engine and perform network mapping and asset discovery. It provides a range of options and functionalities to customize the reconnaissance process.
- Asset Database: The asset database is used to store and manage the findings obtained during the reconnaissance process. It provides a centralized location to navigate and analyze the collected data.
- Open Asset Model: The Open Asset Model (OAM) is a standardized format used by various tools to communicate and understand the assets exposed on the internet. It helps in maintaining a uniform representation of assets for better analysis and integration with other tools.
OWASP Amass can help manage the attack surface by detecting subdomains, IP addresses, and other related assets. It provides a comprehensive view of the network infrastructure, which helps with vulnerability assessment and identifying potential security risks.
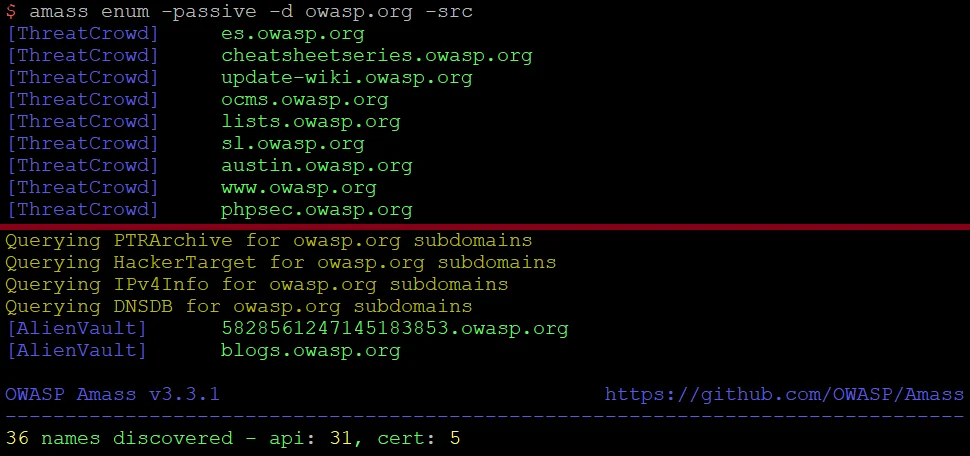
Domain enumeration with OWASP Amass (GitHub)
DefectDojo
There are also open-source tools/services that can import and use findings from various security testing and assessment tools such as Nmap and OpenVAS. One such tool is DefectDojo, an OWASP flagship project.
DefectDojo aids organizations in tracking and managing security vulnerabilities, complementing the capabilities of the tools mentioned in previous sections.
It serves as a centralized platform for overseeing the vulnerability management process; moreover, it integrates with various security testing tools like Nmap and OpenVAS, enhancing their capabilities by offering a comprehensive workflow.
Users can import scan results from Nmap and OpenVAS into DefectDojo, where they can efficiently track and prioritize vulnerabilities, assign tasks to team members, and monitor progress.
In summary, DefectDojo complements tools like Nmap and OpenVAS by providing a structured approach.
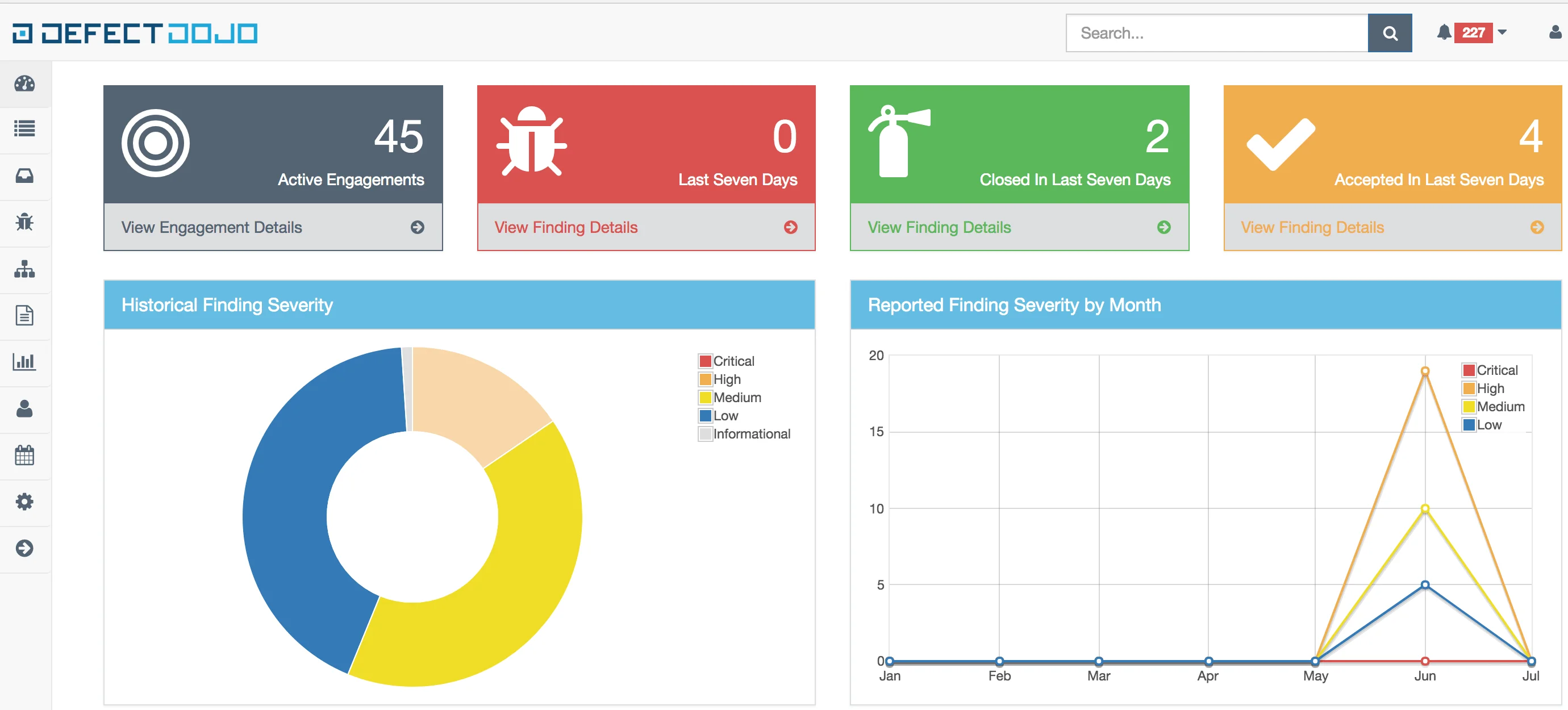
DefectDojo dashboard
IVRE/DRUNK
IVRE (Instrument de veille sur les réseaux extérieurs), also referred to as DRUNK (Dynamic Recon of Unknown NetworKs), is an open-source framework designed for network reconnaissance and attack surface management.
Released under the GNU General Public License, IVRE is freely accessible and its source code is hosted on GitHub.
The tool enables security professionals to evaluate network security by uncovering potential vulnerabilities, misconfigurations, and other security issues. IVRE supports a range of data gathering techniques, including both active methods like scanning with Nmap and Masscan, and passive approaches such as network traffic analysis with tools like Bro, Argus, Nfdump, and p0f.
Users can explore and analyze collected data through CLI tools, a Python API, or the web interface provided by IVRE.
GitHub preview of the IVRE framework
While these open-source tools are useful for monitoring your attack surface, SOCRadar XTI allows you to easily implement an all-encompassing strategy.
SOCRadar’s Attack Surface Management (ASM) module discovers and monitors your organization’s assets in real time, providing you with insights into your asset inventory, alerting you in case of security issues. SOCRadar’s alarms provide quick insights, allowing you to react quickly to security threats and easily initiate response processes.
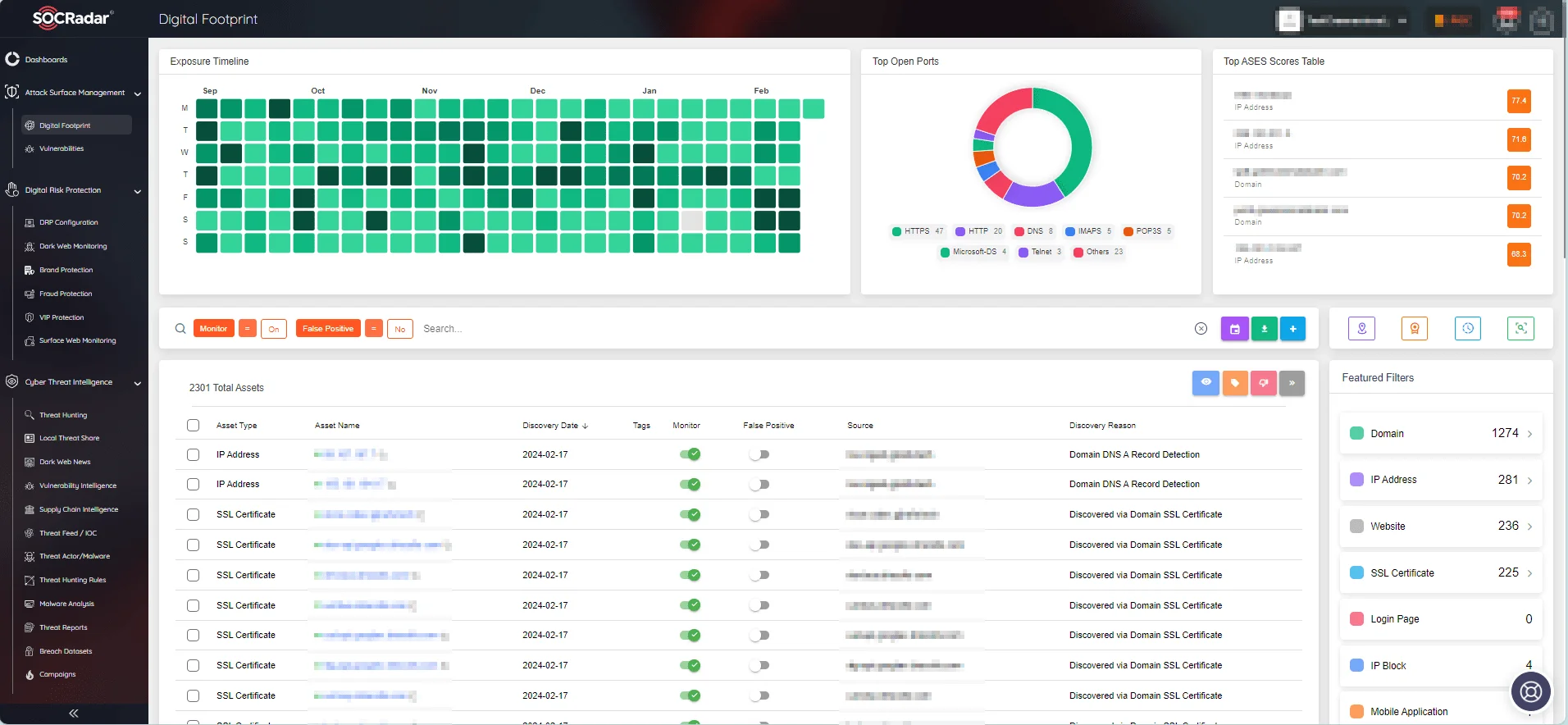
With the ASM module, you can keep track of your digital footprint.
SOCRadar also provides continuous monitoring for vulnerabilities affecting your assets, ensuring that you have timely access to actionable intelligence in order to mitigate threats before they are exploited.
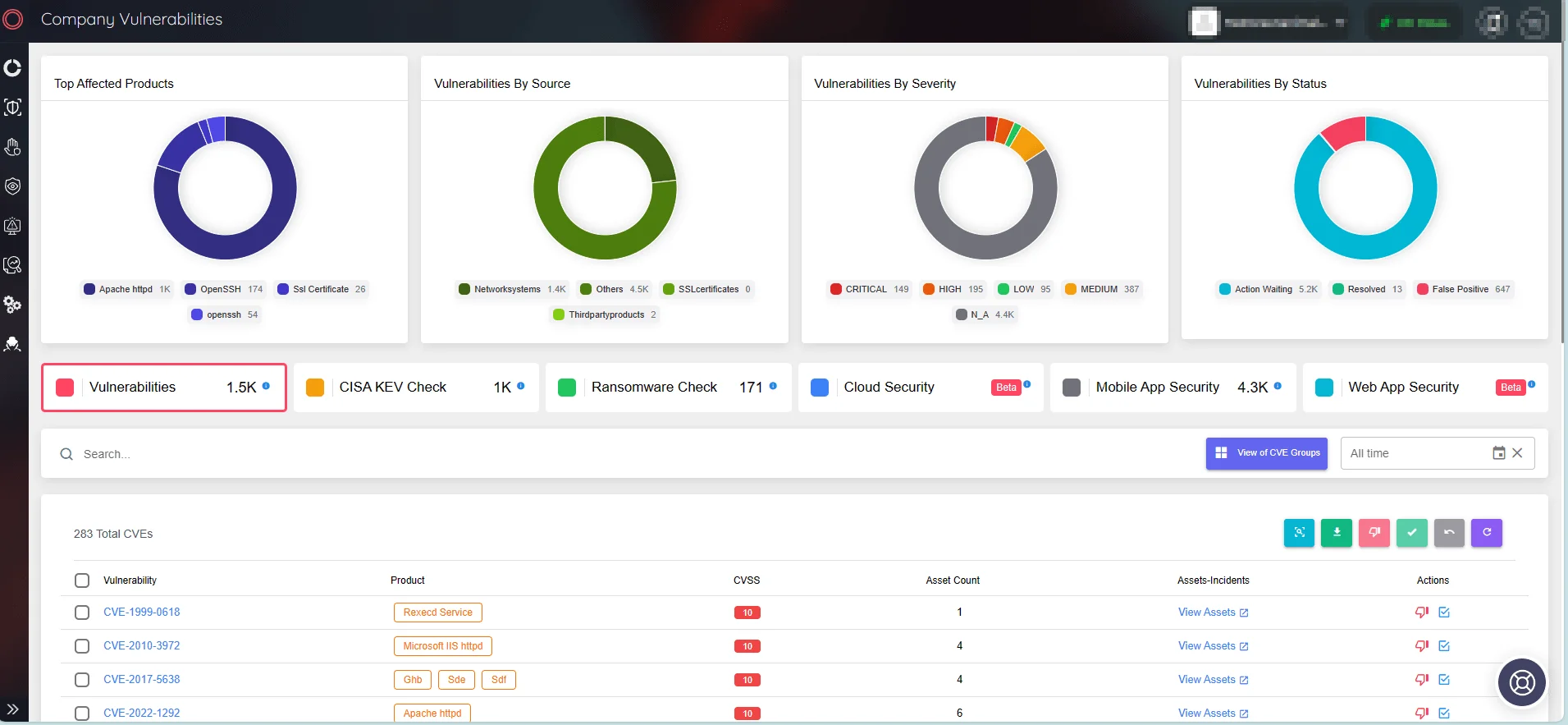
View company vulnerabilities through SOCRadar’s ASM. You can access further details on any identified vulnerability through the Vulnerability Intelligence module.
Conclusion
The proactive management of your attack surface is not a one-time task but a continuous endeavor. The open-source tools we explored today provide a cost-effective and collaborative foundation, empowering organizations of all sizes to strengthen their cybersecurity posture.
As you navigate the intricate digital landscape, the utilization of open-source solutions like Nmap, OpenVAS, DefectDojo, and others can prove very effective, both integration and cost-wise.
However, in a world where cyber threats are relentless, a unified approach becomes vital. SOCRadar XTI can serve as a key solution in this defense, offering a holistic perspective that goes beyond individual tools.
You can also explore our “Top 5 Free Attack Surface Management Tools” article, which complements the topic of this blog post, guiding you towards additional tools for enhancing your attack surface management practices.




































