
Ivanti Connect Secure and Policy Secure Gateways Vulnerable to DoS and Code Execution (CVE-2024-21894)
Ivanti recently released patches to fix multiple vulnerabilities found in their popular Connect Secure (ICS) and Policy Secure VPN gateways: CVE-2024-21894, CVE-2024-22053, CVE-2024-22052, and CVE-2024-22023.
These vulnerabilities present significant risks, as they can be exploited by unauthenticated attackers to compromise network infrastructure, steal sensitive data, and even execute arbitrary code. Of particular concern is that these vulnerabilities can be exploited without any user interaction.
What is CVE-2024-21894 about? Details of the high-severity Ivanti VPN flaws
The most severe vulnerabilities in the update are identified as CVE-2024-21894 and CVE-2024-22053, both with a high-severity CVSS score of 8.2. These vulnerabilities impact the IPSec component of Ivanti Connect Secure and Ivanti Policy Secure gateways, presenting heap overflow weaknesses.
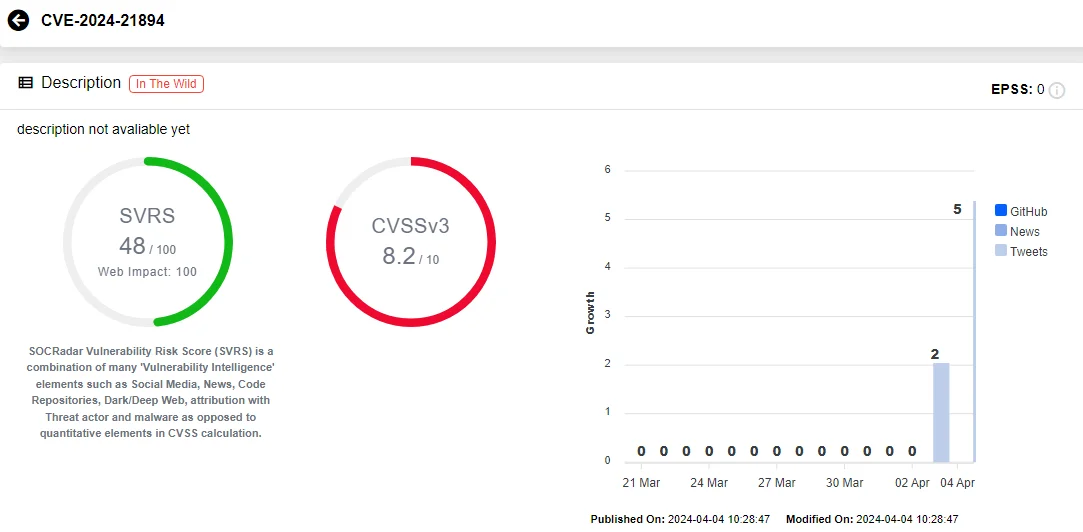
Vulnerability card of CVE-2024-21894 (SOCRadar Vulnerability Intelligence)
Exploiting these vulnerabilities could enable unauthenticated attackers to launch Denial-of-Service (DoS) attacks by sending specially crafted requests that crash the service.
CVE-2024-21894 is especially concerning because it can enable attackers to execute arbitrary code under certain conditions. However, Ivanti has not disclosed which specific configurations are vulnerable to this exploit.
Despite the fact that Ivanti has not yet disclosed any instances of exploitation, the company strongly suggests patching right away in order to reduce any potential risks.
The latest Ivanti update also addresses two other vulnerabilities: CVE-2024-22052 and CVE-2024-22023. While these vulnerabilities have lower severity scores of 7.5 and 5.3 on the CVSS scale, respectively, they still pose significant risks.
CVE-2024-22052 is another flaw affecting the IPSec component, specifically a null pointer dereference issue. On the other hand, CVE-2024-22023 impacts the SAML component and is classified as an XML entity expansion or XEE vulnerability.
Both vulnerabilities carry the risk of enabling Denial-of-Service (DoS) attacks.
Which versions of Ivanti Connect Secure (ICS) and Policy Secure gateways are affected?
Ivanti’s patches cover both the Ivanti Connect Secure (ICS) and Ivanti Policy Secure gateways, addressing the vulnerabilities across all supported versions, from 9.x to 22.x.
How many instances are vulnerable to CVE-2024-21894?
Previously, the Cybersecurity and Infrastructure Security Agency (CISA) issued Emergency Directive ED 24-01 to highlight the urgent threat posed by vulnerabilities in Ivanti systems.
We have seen attackers exploit such VPN appliance vulnerabilities to target organizations across various sectors, including government, military, telecommunications, technology, finance, and aviation.
Additionally, a Shodan search reveals nearly 30,000 Connect Secure VPN gateways currently exposed online, indicating a widespread risk.
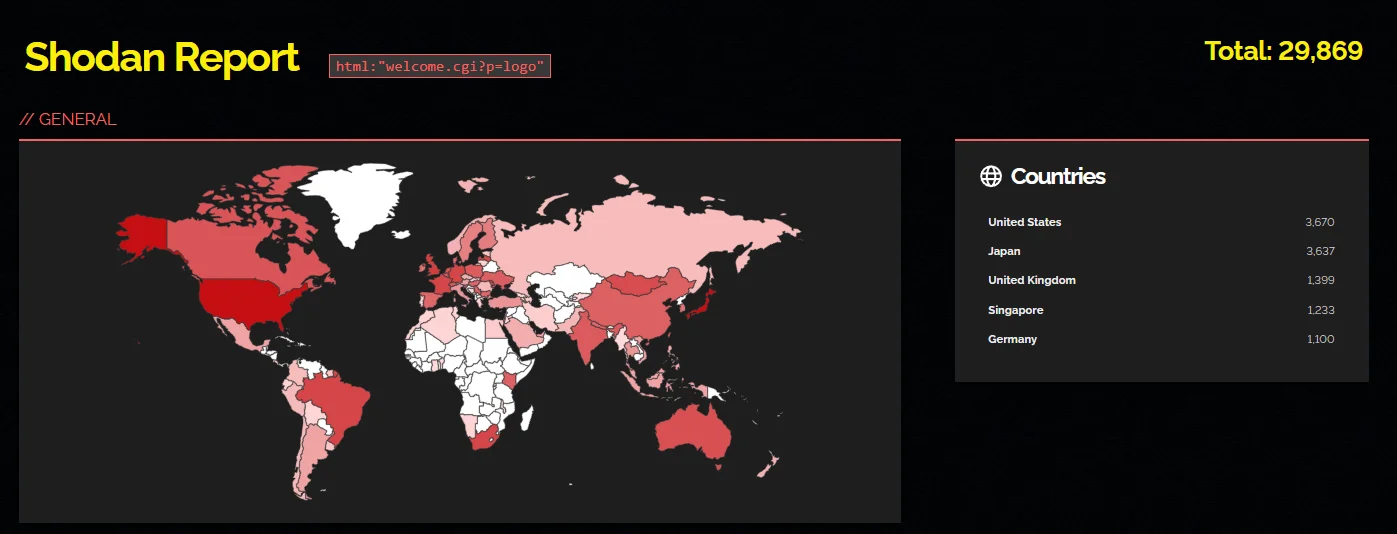
Shodan results for exposed Ivanti VPN gateways
On April 4, CISA reiterated the importance of the recent Ivanti vulnerabilities (CVE-2024-21894, CVE-2024-22053, CVE-2024-22052, and CVE-2024-22023) and issued an alert to underscore Ivanti’s release of security patches for them. The agency urges users and administrators to promptly apply the required patches.
How can you secure Ivanti VPN appliances against these vulnerabilities?
Ivanti has released patch versions for both Ivanti Connect Secure and Ivanti Policy Secure gateways.
For Ivanti Connect Secure, the patch versions include 22.1R6.2, 22.2R4.2, 22.3R1.2, 22.4R1.2, 22.4R2.4, 22.5R1.3, 22.5R2.4, 22.6R2.3, 9.1R14.6, 9.1R15.4, 9.1R16.4, 9.1R17.4, and 9.1R18.5.
For Ivanti Policy Secure, the patch versions are 22.4R1.2, 22.5R1.3, 22.6R1.2, 9.1R16.4, 9.1R17.4, and 9.1R18.5.
Customers can access the patches and the updated External Integrity Checker Tool through the standard download portal provided by Ivanti. For more details and guidance on applying the patches, refer to Ivanti’s advisory.
Continuous Monitoring for Enhanced Vulnerability Management
SOCRadar’s solutions can help strengthen your organization’s vulnerability management. With SOCRadar’s Vulnerability Intelligence and Attack Surface Management (ASM), you can stay up to date on the latest security vulnerabilities while effectively protecting your products and software.
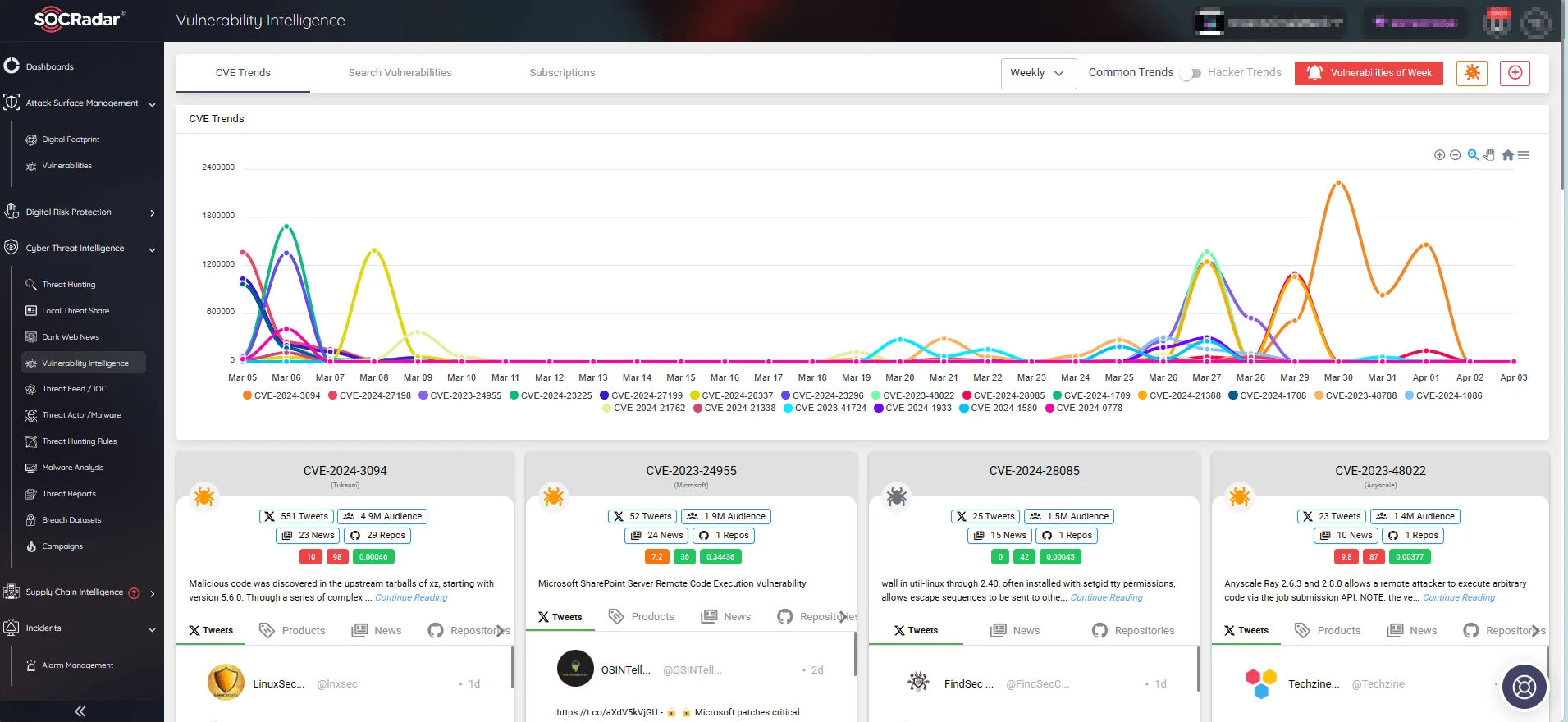
Follow CVE and exploitation trends with SOCRadar’s Vulnerability Intelligence
SOCRadar helps to maintain the security of digital assets within your organization’s ecosystem by monitoring them continuously and sending timely alerts.
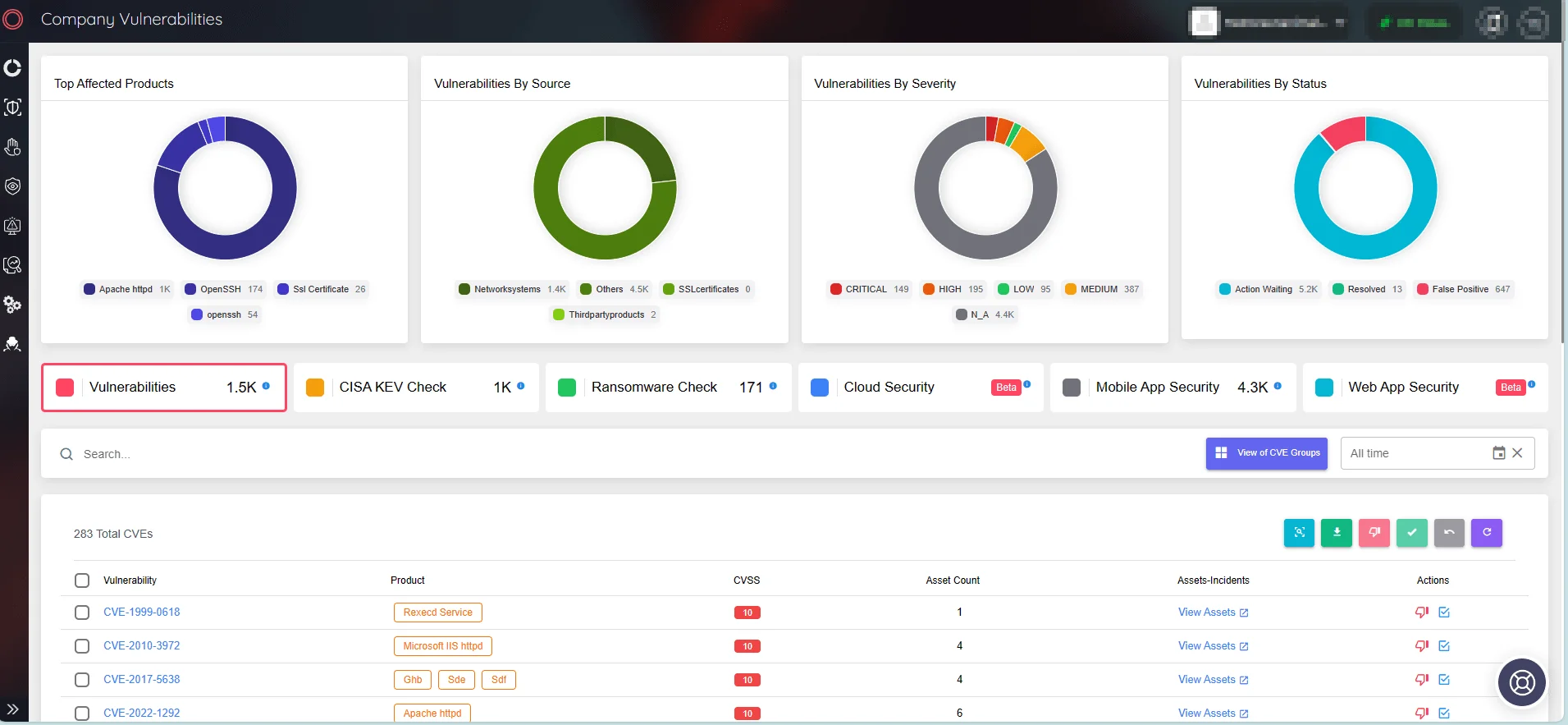
Monitor Company Vulnerabilities via SOCRadar’s ASM




































